Current status
Project is looking for new maintainers, please see the Issue #22.
About
This was a cheat-sheet for a single-user installation of Windows 10 build 1909, also known as "19H2".
Level 3 baseline with additional customizations: less network noise, focus on single-user workstation, etc.

If you are looking for something more of a *nix flavour, check-out the Playbook.
Purpose of the project
Allow Windows users to control the operating system they own have licensed for a limited usage from Microsoft.
Project goals
- Educate users about Windows security capabilites and allow them to enable those in a controlled manner.
- Reduce Microsoft telemetry to the bare minimum. Remove advertising and tracking whenever possible.
- Defer the "feature" updates to counter the appalling quality of what it traditionally shoveled upon the home users.
Project scope
Microsoft Windows 10 on x86-64.
Foreword
Great care should be taken when using commercial operating system with "post-sale monetisation" as a part of its business model. Make no mistake as to what is a product and where profits are coming from.
Rationale
One might ask, — "Why to bother with MS product while there are better *nix-based operating systems?"
At present, main considerations are:
-
Ability to use well-tested FDE that it tied to TPM and user-supplied secret. While it is possible to implement something similar via
keyscriptin/etc/crypttab, this is not a default modus operandi of LUKS.Linux users can use
clevis, however "TPM in conjunction with user password" with automatic roll-over is not supported by any major Linux distribution as in Q1 2020. -
Commercial-grade Type-1 hypervisor.
-
Application firewall with the WFP layer that allows building additional rules on top of the same engine.
Usable GUIs to manage WFP and CLI for the Windows Firewall itself. -
Handy software that is not available under Linux or *BSD.
-
Good hardware support.
Mode of operation
Main Windows installation has whitelisted access only to the practically necessary services:
- OSCP
- Updates
- NTP
- SSH/sFTP
- Intranet SMB
Changing the system
Number of changes are made using MS-provided "Traffic restriction policy". Multiple settings are applied via direct registry injection instead of a GPO import. I can only quote Microsoft, here:
To turn off Messaging cloud sync: There is no Group Policy corresponding to this registry key.
and here:
Note: There is no Group Policy to turn off the Malicious Software Reporting Tool diagnostic data.
Even then, registry "tweaks" are taken from Microsoft documentation for the specific build version.
Known limitations
- Cortana is limited to the Start menu search.
- No access to the microphone, camera and Bluetooth by default
- Ability to log-in via "Microsoft account" is disabled.
- Windows search is not allowed to send queries back to MS/Bing.
- Disabled "Network Connectivity Probe" (NCSI).
- AppX packages are severely limited in what they can access.
- "Activity feed" is disabled.
- ipv6 is disabled by default.
- "Microsoft store" is disabled.
- "Application Compatibility" is disabled.
- "Game DVR" and "XBox" are disabled.
Before installation
- Recognize that you are dealing with the closed-source, SaaS-like operating system.
To give an idea about the "Microsoft world", these are enabled by default:
Automatic learning enables the collection and storage of text and ink written by the user in order to help adapt handwriting recognition to the vocabulary and handwriting style of the user.
Text that is collected includes all outgoing messages in Windows Mail, and MAPI enabled email clients, as well as URLs from the Internet Explorer browser history. The information that is stored includes word frequency and new words not already known to the handwriting recognition engines (for example, proper names and acronyms).
Deleting email content or the browser history does not delete the stored personalization data. Ink entered through Input Panel is collected and stored.
"When you interact with your Windows device by speaking or typing, Microsoft collects speech, inking, and typing information – including information about your Calendar and People"
Windows "Defender":
Information collected includes file data (such as file names, sizes, and hashes), process data (running processes, hashes), registry data, network connection data (host IPs and ports), and device details (such as device identifiers, names, and the operating system version).
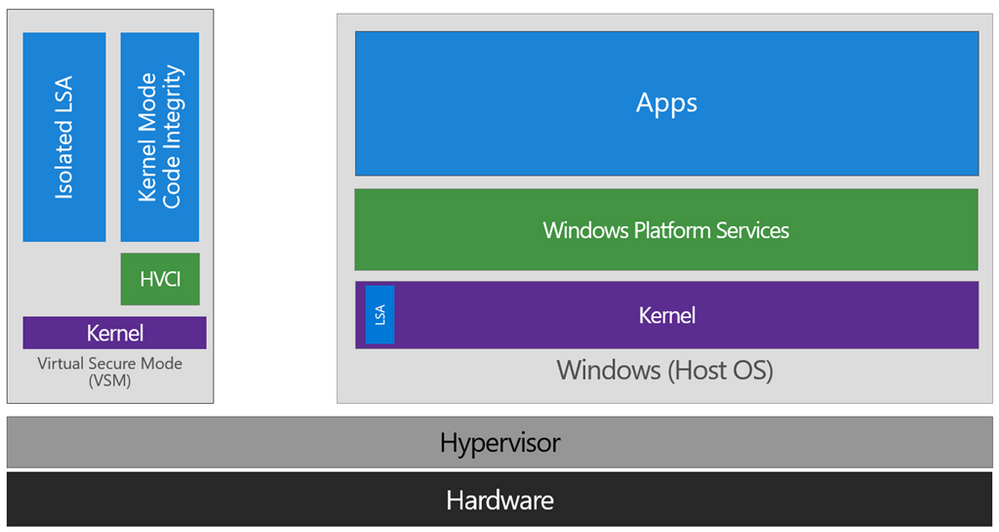
- Be aware that you will be enabling Hypervisor-protected code integrity (HVCI) which imposes significant performance penalty on all Intel CPUs released before "7th generation" and AMD processors prior to "Ryzen 2". To quote Mark Russinovich and Alex Ionescu:
"The Secure Kernel relies on the Mode-Based Execution Control (MBEC) feature, if present in hardware, which enhances the SLAT with a user/kernel executable bit, or the hypervisor’s software emulation of this feature, called Restricted User Mode (RUM)."
After we are done, your environment will look like this:
 ...plus some more VMs on the side.
...plus some more VMs on the side.
- Remember about performance hit from countermeasures against 2019 side-channel attacks. Down the track, you can obtain CPU stepping by running
wmic cpu get captionin PowerShell and, if using Intel, comparing against this list. Now, the hardware upgrade might be a wise choice. - Un-plug ethernet if present, disable WiFi.
- Install latest BIOS/FWs from a vendor.
- Consider stripping Intel ME using metool or be ready to assess/update/patch using CSME, link above.
- Enable UEFI-native boot, "Secure boot", DEP, VTx/VT-d (or AMD-V).
- In case you are using Intel™, depending on the CPU generation you might consider disabling HyperThreading®.
- On certain SMB platforms IntelTXT® is enabled and not exposed in BIOS which may prevent from disabling HT.
- Sometimes this can be circumvented by using vendor's mass-provisioning tool. For example, HP:
Stdout:.\BiosConfigUtility64.exe /setvalue:"Trusted Execution Technology (TXT)","Disable" /cpwdfile:"pwd.bin" /verbose
<BIOSCONFIG Version="" Computername="WIN" Date="2019/08/31" Time="21:23:19" UTC="10"> <SUCCESS msg="Successfully read password from file" /> <SETTING changeStatus="skip" name="Trusted Execution Technology (TXT)" returnCode="18"> <OLDVALUE><![CDATA[Enable]]></OLDVALUE> <VALUE><![CDATA[Disable]]></VALUE> </SETTING> <SUCCESS msg="No errors occurred" /> <Information msg="BCU return value" real="0" translated="0" /> </BIOSCONFIG>
- Afterwards, you should be able to disable HT:
.\BiosConfigUtility64.exe /setvalue:"Intel (R) HT Technology","Disable" /cpwdfile:"pwd.bin" /l /verbose
- Reader is encouraged to check the numerous vulnerabilities affecting Intel CPUs. With no end in sight for this maddness. Vote with your wallet.
During installation
- Keep machine disconnected from the Internet
- Opt-out from all personal data collection when asked. This means answering "no" to every single question.
After installation
- Copy to the target machine via local means:
- This repository
- pfSense installation ISO
- Copy
LGPO.exefrom./ToolstoC:\Windows\system32\.
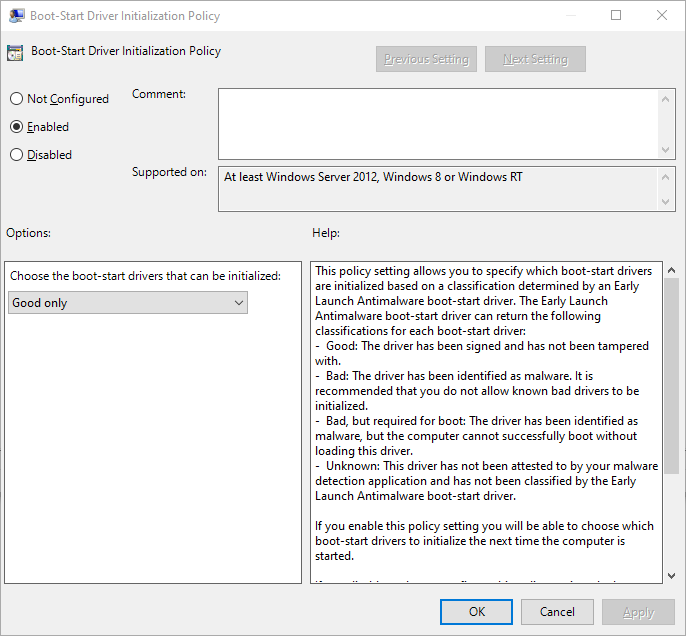
Enable HVCI and Credential Guard
-
From
./Tools/dgreadiness_v3.6, launch DG readiness tool.- Temporarily change execution policy for PowerShell scripts:
Set-ExecutionPolicy -ExecutionPolicy AllSigned - Check current status:
.\DG_Readiness_tool_v3.6.ps1 -Ready - Enable:
.\DG_Readiness_tool_v3.6.ps1 -Enable - Looks like this?
- Good. Don't forget to switch the policy back:
Set-ExecutionPolicy -ExecutionPolicy Restricted
- Temporarily change execution policy for PowerShell scripts:
-
Reboot
-
If curious (as you should be), check the status and compare against documentation:
Get-CimInstance -Namespace ROOT\Microsoft\Windows\DeviceGuard -ClassName Win32_DeviceGuard
In general, output should look like this:
AvailableSecurityProperties : {1, 2, 3, 4, 5, 7} # Depends on the hardware support CodeIntegrityPolicyEnforcementStatus : 0 InstanceIdentifier : long-id-here RequiredSecurityProperties : {0} # SecurityServicesConfigured : {0} # Depends on the hardware support SecurityServicesRunning : {0} # UsermodeCodeIntegrityPolicyEnforcementStatus : 0 Version : 1.0 VirtualizationBasedSecurityStatus : 0 PSComputerName : COMPUTERNAME
Apply baseline policies
Security
-
Navigate to
./Tools/baseline_security/Scriptsand:Set-ExecutionPolicy -ExecutionPolicy Unrestricted .\Baseline-LocalInstall.ps1 -Win10NonDomainJoined
-
Add attack surface reduction rules.
$asrs = @("BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550", # Block executable content from email client and webmail "D4F940AB-401B-4EFC-AADC-AD5F3C50688A", # Block all Office applications from creating child processes "3B576869-A4EC-4529-8536-B80A7769E899", # Block Office applications from creating executable content "75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84", # Block Office applications from injecting code into other processes "D3E037E1-3EB8-44C8-A917-57927947596D", # Block JavaScript or VBScript from launching downloaded executable content "5BEB7EFE-FD9A-4556-801D-275E5FFC04CC", # Block execution of potentially obfuscated scripts "92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B", # Block Win32 API calls from Office macro "01443614-cd74-433a-b99e-2ecdc07bfc25", # Block executable files from running unless they meet a prevalence, age, or trusted list criterion "c1db55ab-c21a-4637-bb3f-a12568109d35", # Use advanced protection against ransomware "9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2", # Block credential stealing from the Windows local security authority subsystem (lsass.exe) "d1e49aac-8f56-4280-b9ba-993a6d77406c", # Block process creations originating from PSExec and WMI commands "b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4", # Block untrusted and unsigned processes that run from USB "26190899-1602-49e8-8b27-eb1d0a1ce869", # Block Office communication application from creating child processes "7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c", # Block Adobe Reader from creating child processes "e6db77e5-3df2-4cf1-b95a-636979351e5b") # Block persistence through WMI event subscription foreach ($rule in $asrs) { Add-MpPreference -AttackSurfaceReductionRules_Ids $rule -AttackSurfaceReductionRules_Actions Enabled }
-
Check that rules are applied correctly:
(Get-MpPreference | Select-Object -ExpandProperty AttackSurfaceReductionRules_Ids).Count -eq 15
-
Check antimalware:
Get-MpComputerStatus | Select-Object -Property "*enabled*" AMServiceEnabled : True AntispywareEnabled : True AntivirusEnabled : True BehaviorMonitorEnabled : True IoavProtectionEnabled : True NISEnabled : True OnAccessProtectionEnabled : True RealTimeProtectionEnabled : True
-
Set Windows Defender to run its child process(es) from within AppContainer:
setx /M MP_FORCE_USE_SANDBOX 1
-
Reboot
Optional, but convenient:
- Open "Group Policy editor", navigate to
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options- Change "User Account Control: Behavior of the elevation prompt for standard users" to "Prompt for credentials on the secure desktop"
- Navigate to:
Computer Configuration\Policies\Administrative Templates\Windows Components\File Explorer- Enable "Show hibernate in the power options menu"
Traffic restriction
-
Navigate to
./Tools/baseline_trafficand:cp ..\LGPO\LGPO.exe .\Tools\ .\RestrictedTraffic_ClientEnt_Install.cmd
- Accept the terms.
-
Open "Local group policy editor"
- Navigate to "Administrative templates --> Windows components --> Windows update"
- Ensure all policies are set to "Not configured"
-
Reboot
Remove pre-installed AppX packages
- Navigate to
./Tools/Scripts. - In elevated PowerShell:
apps.ps1
Clean-up profiles
- Create at least one new user profile
- Log in as the newly created administrator
- Remove the old account, choose "delete files"
- Reboot
Install stoptracking changes
As some of the changes are applied to HKCU hive, for each user, run:
- In elevated
cmd.exe:windows.batedge.bat
- In elevated PowerShell:
interfaces.ps1gpupdate /force
- Reboot
Speculative execution attacks
-
Use
tools/mdstoolsto assess the damage. -
From
tools/SpeControl:Import-Module -name .\SpeculationControl.psm1 Get-SpeculationControlSettings -Verbose
If output is unsatisfactory...
- Enable CVE-2018-3639 mitigations, as per MS article,
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 72 /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d "1.0" /f
- Reboot and compare output of
Get-SpeculationControlSettingsagainst the documentation.
Misc
-
Set execution policy back:
Set-ExecutionPolicy -ExecutionPolicy Restricted
-
Enable controlled folder access:
Set-MpPreference -EnableControlledFolderAccess Enabled
System CA
Adjust content as necessary:
Enable Bitlocker
-
Open policy editor and filter for: "Configure TPM platform validation for native UEFI firmware configurations".
-
Enable PCR banks according to your hardware, here is the comprehensive list with explanations.
Good start on a relatively modern device with TPM 2.0 would be0,1,.......TODO -
Use
manage-bdeto set-up BitLocker and add/remove recovery agents.- Double-check that Bitlocker is disabled for the system drive:
.\manage-bde.exe -protectors -get C:
- If result is negative, add TPM and PIN:
.\manage-bde.exe -protectors -add -tp C:
- Until the above is confirmed working, add temporary recovery key:
.\manage-bde.exe -protectors -add -rp C:
Write-down the numerical password, you will need it if machine refuses to boot with the chosen set of PCR banks.
-
If computer has started successfully and
Manage-BDE -protectors -get C:returns data set at step #1... -
Add file protectors instead of the pre-generated numerical sequence:
.\manage-bde.exe -protectors -delete -t RecoveryPassword C: .\manage-bde.exe -protectors -add -rk X:\WHERE_TO_STORE_KEY C:
N.B. Don't forget to securely wipe device "X" after the key is transferred to a proper location.
GPOs
Virtual Machines
As you remember, "commercial-grade hypervisor" was listed as one of the advantages. Time to use it.
V-Switch setup
- In Hyper-V Manager, open "Virtual Switch Manager".
- Create a new switch:
- Type: external
- Map to the physical interface
- Un-tick "Allow management operating system to share this network adapter"
Router
We will be using pfSense to setup a router that filters traffic, acts as a VPN client and transparent proxy.
pfSense Installation
- Download ISO for AMD64.
- Create new VM, allocate 2 or 4 CPU cores, 2Gb of RAM and 8Gb disk.
- Disable "dynamic memory" function.
- Setup networking:
- Add second network adapter.
- Connect it to the "external" switch.
- Setup distinct MAC addresses on both adapters.
- Proceed with installation, reboot.
Initial setup
- Connect to the VM from Hyper-V Manager.
- Select "1" from the on-screen menu.
- Choose WAN interface, this corresponds to the "external" switch.
- Assign IPs to both adapters.
- Open GUI via web-browser and proceed with the guided setup.
- Under "System / Advanced / Networking":
- Disable "Allow ipv6"
- You might need to disable hardware checksum offloading
Please refer to this note for details.
- Under "System / Advanced / Miscellaneous":
- Un-tick "Installation Feedback"
- Enable AES-NI acceleration
- Power-off and create VM snapshot.
Transparent proxy
- Enable DNS resolver at "Services / DNS Resolver / General Settings".
- Navigate to "SystemPackage / ManagerPackage / Installer".
- Install
squidandsquidGuard. - Create CA at "Sytem / Cert. Manager"
- Open "Squid proxy server" from Services menu.
- "General" tab:
- Tick "Enable Squid proxy"
- Enable "Transparent HTTP Proxy" and "Bypass Proxy for Private Address Destination".
- Set "SSL/MITM Mode" to "Splice All"
- Set "X-Forwarded Header Mode" to "transparent".
- Save
- "Local cache" tab:
- Set memory cache size to 512mb
- Set maximum object size to keep in memory to 512
- Set hard disk cache size to 0
- Save
- "General" tab:
- Open "SquidGuard proxy filter" from Services menu.
- "General settngs" tab:
- Tick "Enable"
- Enable logging and log rotation
- Save
- "Target categories" tab:
- Create new category
- Add the following domains:
ctldl.windowsupdate.com sls.microsoft.com mp.microsoft.com wustat.windows.com windowsupdate.com - Create target categories
- TODO
- Go back to the "General" tab and click green "Apply" button
- "General settngs" tab:
After the machine is online
- After the Windows is activated, execute from elevated
cmd.exe:reg add "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\CurrentVersion\Software Protection Platform" /t REG_DWORD /v NoGenTicket /d 1 /f sc config sppsvc start=disabled
Documentation
Papers
Tools
This guide accepts no closed-source utilities that promise to "fix Windows privacy". Author has rather dim view on such tools and prefers to rely on empirical evidence and collected data rather than a promise. When possible, instruments provided by Microsoft are used instead of a 3rd-party application.
- MS Security Compliance Toolkit
- GPO and Policy Analyzer
- Wireshark and MS Network Monitor
- Sysinternals
- Intel CSME
Questions
- Why not DISM?
- This framework is oriented towards the wide audience. Some of them might not have an access to a known clean computer with Windows 10 installation, others could lack knowledge of assembling the base image and are at risk of ending-up with botched installation.
- Why internet access from the "main" Windows installation is so restricted?
- Vastly reduces an impact of coersive telemtry across the whole software stack.
- Makes operating reverse shell a little bit trickier.
- Why Windows version 2004 aka "20H1" is not supported?
- 1909 is a mature and stable release supported by Microsoft until May 2021 for Home/Pro/WS/IoT and until May 2022 for Enterprise/Education.
- At the time of wiriting, relevant policies for 20H1 were not published or tested.
- Microsoft is known to introduce updates that go as far as deleting user files
- https://answers.microsoft.com/en-us/windows/forum/all/cumulative-updates-may-12th-2020/3a51c803-1114-4551-bca2-e5a610900f52?LastReply=true#LastReply&page=1