hot3eed / Xpcspy
Licence: apache-2.0
Bidirectional XPC message interception and more. Powered by Frida
Stars: ✭ 101
Programming Languages
typescript
32286 projects
Projects that are alternatives of or similar to Xpcspy
Frida Fuzzer
This experimetal fuzzer is meant to be used for API in-memory fuzzing.
Stars: ✭ 415 (+310.89%)
Mutual labels: frida
Dwarf
Full featured multi arch/os debugger built on top of PyQt5 and frida
Stars: ✭ 916 (+806.93%)
Mutual labels: frida
Rms Runtime Mobile Security
Runtime Mobile Security (RMS) 📱🔥 - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime
Stars: ✭ 1,194 (+1082.18%)
Mutual labels: frida
Dexcalibur
[Official] Android reverse engineering tool focused on dynamic instrumentation automation. Powered by Frida. It disassembles dex, analyzes it statically, generates hooks, discovers reflected methods, stores intercepted data and does new things from it. Its aim is to be an all-in-one Android reverse engineering platform.
Stars: ✭ 512 (+406.93%)
Mutual labels: frida
Frida Scripts
A collection of my Frida.re instrumentation scripts to facilitate reverse engineering of mobile apps.
Stars: ✭ 665 (+558.42%)
Mutual labels: frida
House
A runtime mobile application analysis toolkit with a Web GUI, powered by Frida, written in Python.
Stars: ✭ 910 (+800.99%)
Mutual labels: frida
Frida Gum
Cross-platform instrumentation and introspection library written in C
Stars: ✭ 357 (+253.47%)
Mutual labels: frida
Qbdi
A Dynamic Binary Instrumentation framework based on LLVM.
Stars: ✭ 801 (+693.07%)
Mutual labels: frida
Jnitrace
A Frida based tool that traces usage of the JNI API in Android apps.
Stars: ✭ 534 (+428.71%)
Mutual labels: frida
Ios debugger challenge
A playground for run-time iOS app inspection
Stars: ✭ 39 (-61.39%)
Mutual labels: frida
Extracttvpasswords
tool to extract passwords from TeamViewer memory using Frida
Stars: ✭ 444 (+339.6%)
Mutual labels: frida
Dbi Stuff
Resources About Dynamic Binary Instrumentation and Dynamic Binary Analysis
Stars: ✭ 80 (-20.79%)
Mutual labels: frida
Frida Core
Frida core library intended for static linking into bindings
Stars: ✭ 398 (+294.06%)
Mutual labels: frida
Jnitrace Engine
Engine used by jnitrace to intercept JNI API calls.
Stars: ✭ 94 (-6.93%)
Mutual labels: frida
xpcspy - Bidirectional XPC message interception and more
Features:
- Bidirectional XPC message interception.
- iOS and macOS support.
-
bplist00, and the infamousbplist15deserialization. - Filter by message direction (incoming or outgoing) and service name.
- More to come?
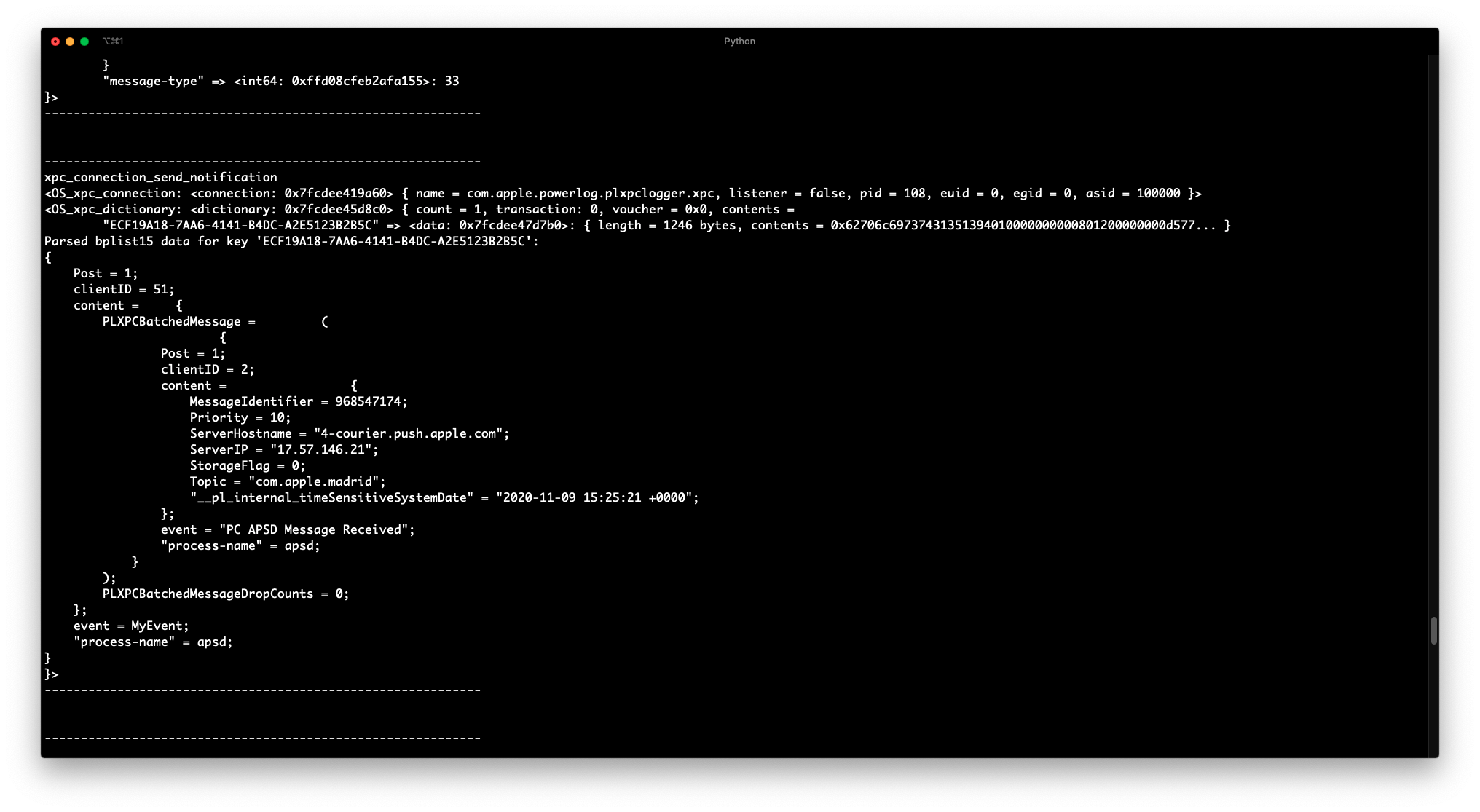
Showcase
Usage: xpcspy [options] target
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-D ID, --device=ID connect to device with the given ID
-U, --usb connect to USB device
-R, --remote connect to remote frida-server
-H HOST, --host=HOST connect to remote frida-server on HOST
-f FILE, --file=FILE spawn FILE
-F, --attach-frontmost
attach to frontmost application
-n NAME, --attach-name=NAME
attach to NAME
-p PID, --attach-pid=PID
attach to PID
--stdio=inherit|pipe stdio behavior when spawning (defaults to “inherit”)
--aux=option set aux option when spawning, such as “uid=(int)42”
(supported types are: string, bool, int)
--runtime=qjs|v8 script runtime to use
--debug enable the Node.js compatible script debugger
--squelch-crash if enabled, will not dump crash report to console
-O FILE, --options-file=FILE
text file containing additional command line options
-t FILTER, --filter=FILTER
Filter by message direction and service name. 'i'
denotes incoming and 'o' denotes outgoing. Service
name can include the wildcard character '*'. For
exmaple 'i:com.apple.*' or 'o:com.apple.apsd'.
-r, --parse Parse XPC dictionary keys that include either
`bplist00` or `bplist16` data.
Installation
pip3 install xpcspy
TODO:
- Add support for
bplist16. - Deserialize data within the parsed
bplists recursively. - Improve script loading performance, kinda slow for some reason.
- Add an option to get the address, perhaps ASLR adjusted, for the XPC event handler, by spawning the process and hooking
xpc_connection_set_event_handler. - Add fancy colors.
- More pretty printing?
FAQ
- Why are you reinventing the wheel?
- I'm not; XPoCe doesn't intercept incoming messages, and doesn't support
bplist00orbplist15. `
- I'm not; XPoCe doesn't intercept incoming messages, and doesn't support
License
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].