JulianHayward / Azure Mg Sub Governance Reporting
Programming Languages
Labels
Projects that are alternatives of or similar to Azure Mg Sub Governance Reporting
AzGovViz - Azure Governance Visualizer
Do you want to get granular insights on your technical Azure Governance implementation? - document it in CSV, HTML and MD (Markdown)?
AzGovViz is a PowerShell based script that iterates your Azure Tenant´s Management Group hierarchy down to Subscription level. It captures most relevant Azure governance capabilities such as Azure Policy, RBAC and Blueprints and a lot more. From the collected data AzGovViz provides visibility on your HierarchyMap, creates a TenantSummary, creates DefinitionInsights and builds granular ScopeInsights on Management Groups and Subscriptions. The technical requirements as well as the required permissions are minimal.
You can run the script either for your Tenant Root Group or any other Management Group that you have read access on.
AzGovViz @ Microsoft Cloud Adoption Framework

|
Listed as tool for the Govern discipline in the Microsoft Cloud Adoption Framework! Included in the Microsoft Cloud Adoption Framework´s Strategy-Plan-Ready-Gov Azure DevOps Demo Generator template. |
AzGovViz release history
Breaking Changes (2021-Feb-28)
- When granting Azure Active Directory Graph API permissions in the background an AAD Role assignment for AAD Group Directory readers was triggered automatically - since January/February 2021 this is no longer the case. Review the updated AzGovViz technical documentation section for detailed permission requirements.
AzGovViz in Action
|
Enterprise-Scale (WingTip) implementation |
Features
-
Hierarchy of Management Groups
- Builds a visual hierarchy of your Management Group setup including count of linked Subscriptions
-
Azure Policy
- Custom Policy definitions
- Scope information
- Policy effect
- If Policy effect is DeployIfNotExists (DINE) will show the specified RBAC Role
- List of assignments
- Usage in custom PolicySet definitions
- Orphaned custom Policy definitions
- List of custom Policy definitions that matches the following criteria:
- Policy definition is not used in any custom PolicySet definition
- No Policy assignment exists for the Policy definition
- List of custom Policy definitions that matches the following criteria:
- Custom PolicySet definitions
- Scope information
- List unique assignments
- List of Policy definitions used
- Orphaned custom PolicySet definitions
- Criteria: no Policy assignment exists for the PolicySet definition
- Custom PolicySet definitions using deprecated built-in Policy definitions
- Policy assignments of deprecated built-in Policy definition
- Policy Exemptions
- Lists all Exemptions (scopes: Management Groups, Subscriptions, ResourceGroups, Resources)
- Enrich information on Exemption scope
- Summary on expired Exemptions
- Policy assignments throughout the entirety of scopes (Management Groups, Subscriptions)
- Core information on Policy assignments
- Advanced information on Policy assignments
- Policy assignment scope (at scope/inheritance)
- Indicates if scope is excluded from Policy assignment
- Indicates if Exemption applies for scope
- Policy/Resource Compliance
- Related RBAC Role assignments (if Policy effect is DeployIfNotExists (DINE))
- Custom Policy definitions
-
Role-Based Access Control (RBAC)
- Custom Role definitions
- List assignable scopes
- Orphaned custom Role definitions
- List of custom Role definitions that matches the following criteria:
- Role definition is not used in any Role assignment
- List of custom Role definitions that matches the following criteria:
- Orphaned Role assignments
- List of Role assignments that matches the following criteria:
- Role definition was deleted although and assignment existed
- Role assignmet's target identity (User, Group, ServicePrincipal) was deleted
- List of Role assignments that matches the following criteria:
- Role assignments throughout the entirety of scopes (Management Groups, Subscriptions)
- Core information on Role assignments
- Advanced information on Role assignments
- Role assignment scope (at scope / inheritance)
- For Role Assignments on Groups the AAD Group members are fully resolved. With this capability AzGovViz can ultimately provide holistic insights on permissions granted
- For identity-type == 'ServicePrincipal' the type (Application/ManagedIdentity) will be reported
- For identity-type == 'User' the userType (Member/Guest) will be reported
- Related Policy assignments (Policy assignment of a Policy definition that uses the DeployIfNotExists (DINE) effect)
- Security & Best practice analysis
- Existence of custom Role definition that reflect 'Owner' permissions
- Role assignments for 'Owner' permissions on identity-type == 'ServicePrincipal'
- Role assignments for 'Owner' permissions on identity-type != 'Group'
- Role assignments for 'UserAccessAdministrator' permissions on identity-type != 'Group'
- Custom Role definitions
-
Blueprints
- Blueprint scopes and assignments
- Orphaned Blueprints
-
Management Groups & limits
- Management Group count and Management Group level depth
- Default Management Group
- Management Groups approaching ARM limits:
- Policy assignment limit
- Policy / PolicySet definition scope limit
- Role assignment limit
-
Subscriptions, Resources & limits
- Subscription insights
- QuotaId, State, Tags, Azure Security Center Secure Score, Cost, Management Group path
- Subscriptions approaching ARM limits:
- ResourceGroup limit
- Subscription Tags limit
- Policy assignment limit
- Policy / PolicySet definition scope limit
- Role assignment limit
- Tag Name usage
- Insights on usage of Tag Names on Subscriptions, ResourceGroups and Resources
- Resources
- Resource Types
- ResourceType count per location
- ResourceType capability for Resource Diagnostics including
- ResourceType count and information if capable for logs including list of available og categories
- ResourceType count and information if capable for metrics
- Lifecyle recommendations for existing Azure Policy definitions that configure Resource diagnostics of type=Log
- Check if Policy definitions hold the latest set of applicable log categories
- Recommendation to create Policy definition for ResourceType if supported
- Lists all PolicyDefinitions that deploy Resource diagnostics of type=log, lists Policy assignments and PolicySet assignments if the Policy defintion is used in a PolicySet definition
- Resource Provider
- Resource Provider state aggregation throughout all Subscriptions
- Explicit Resource Provider state per Subscription
- Resource Locks
- Aggregated insights for Lock and respective Lock-type usage on Subscriptions, ResourceGroups and Resources
- Resource Types
- Subscription insights
-
Azure Active Directory (AAD)
- Insights on those Service Principals where a Role assignment exists (scopes: Management Group, Subscription, ResourceGroup, Resource):
- Type=ManagedIdentity
- Core information on the Service Principal such as related Ids and use case information
- Type=Application
- Secrets and Certificates expiry information & warning
- Report on external Service Principals
- Type=ManagedIdentity
- Insights on those Service Principals where a Role assignment exists (scopes: Management Group, Subscription, ResourceGroup, Resource):
-
Consumption
- Aggregated consumption insights throughout the entirety of scopes (Management Groups, Subscriptions)
Screenshots
HTML file
HierarchyMap
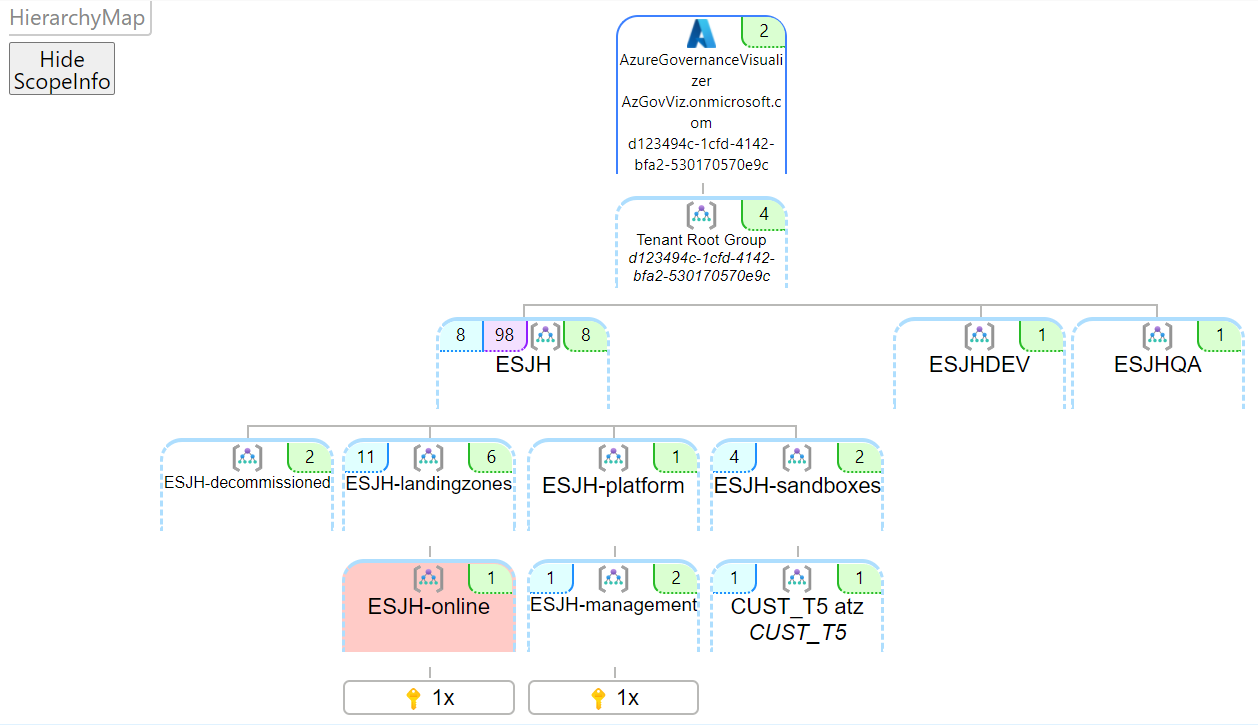
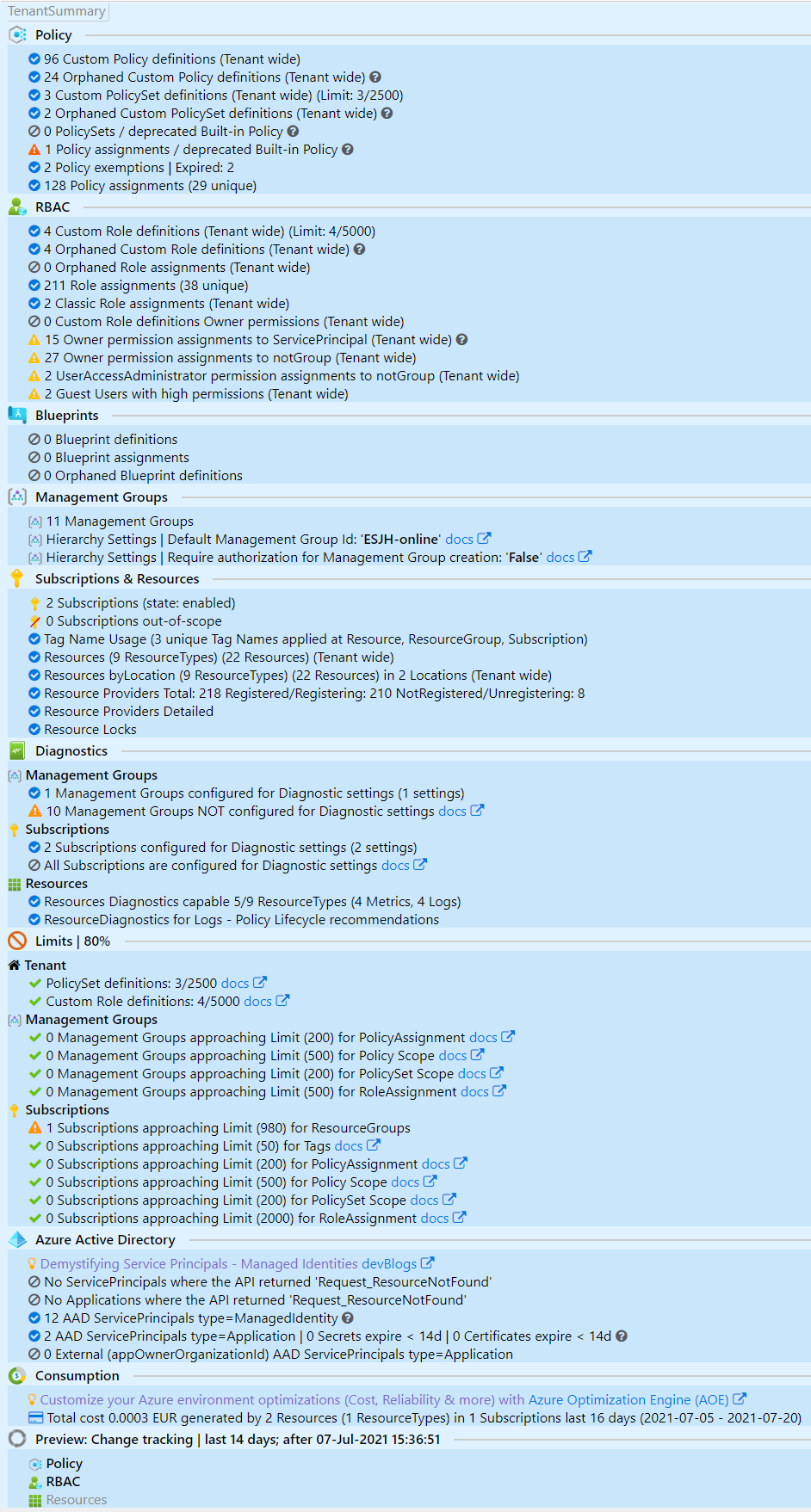
TenantSummary
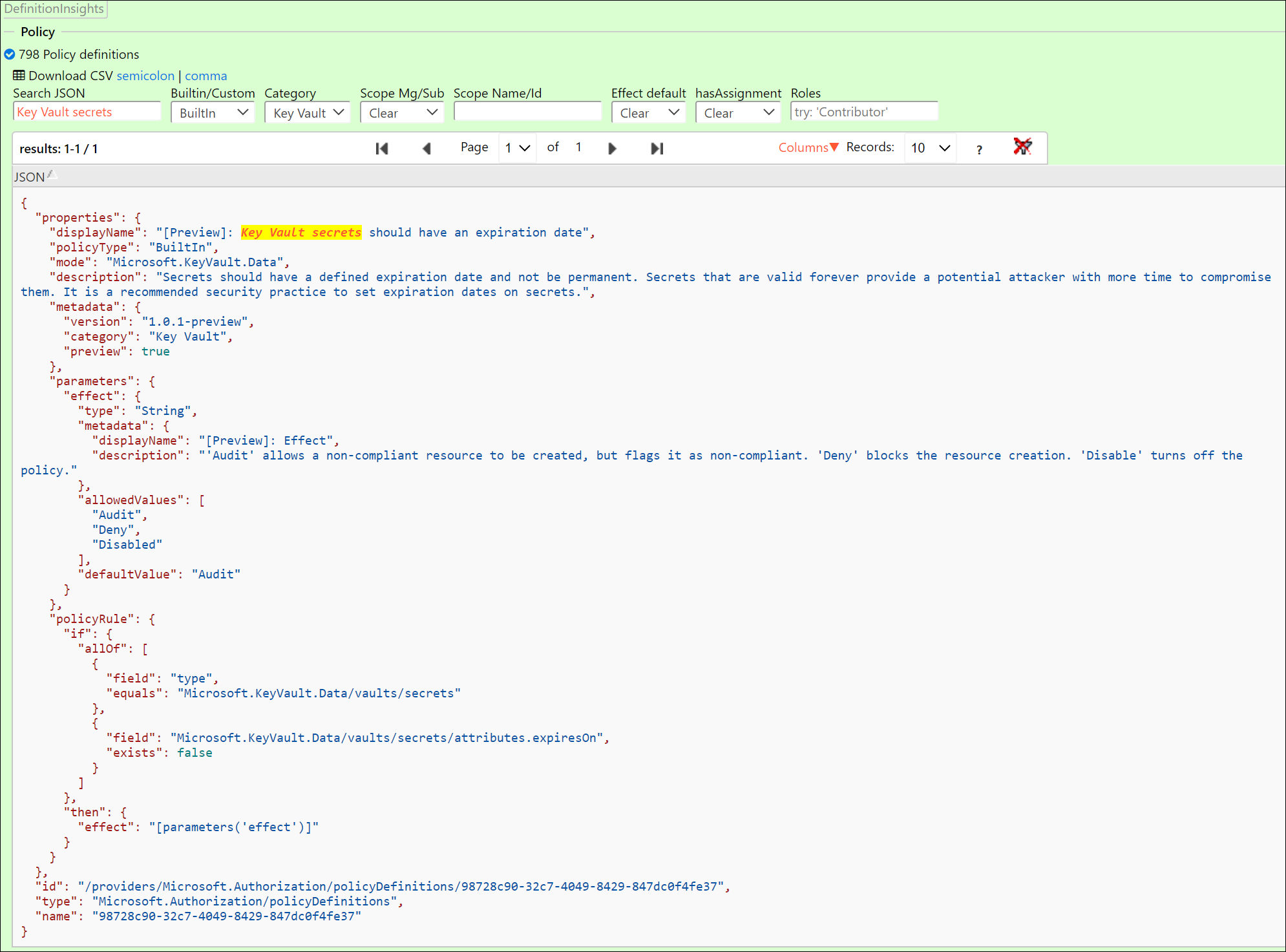
DefinitionInsights
 ScopeInsights
ScopeInsights
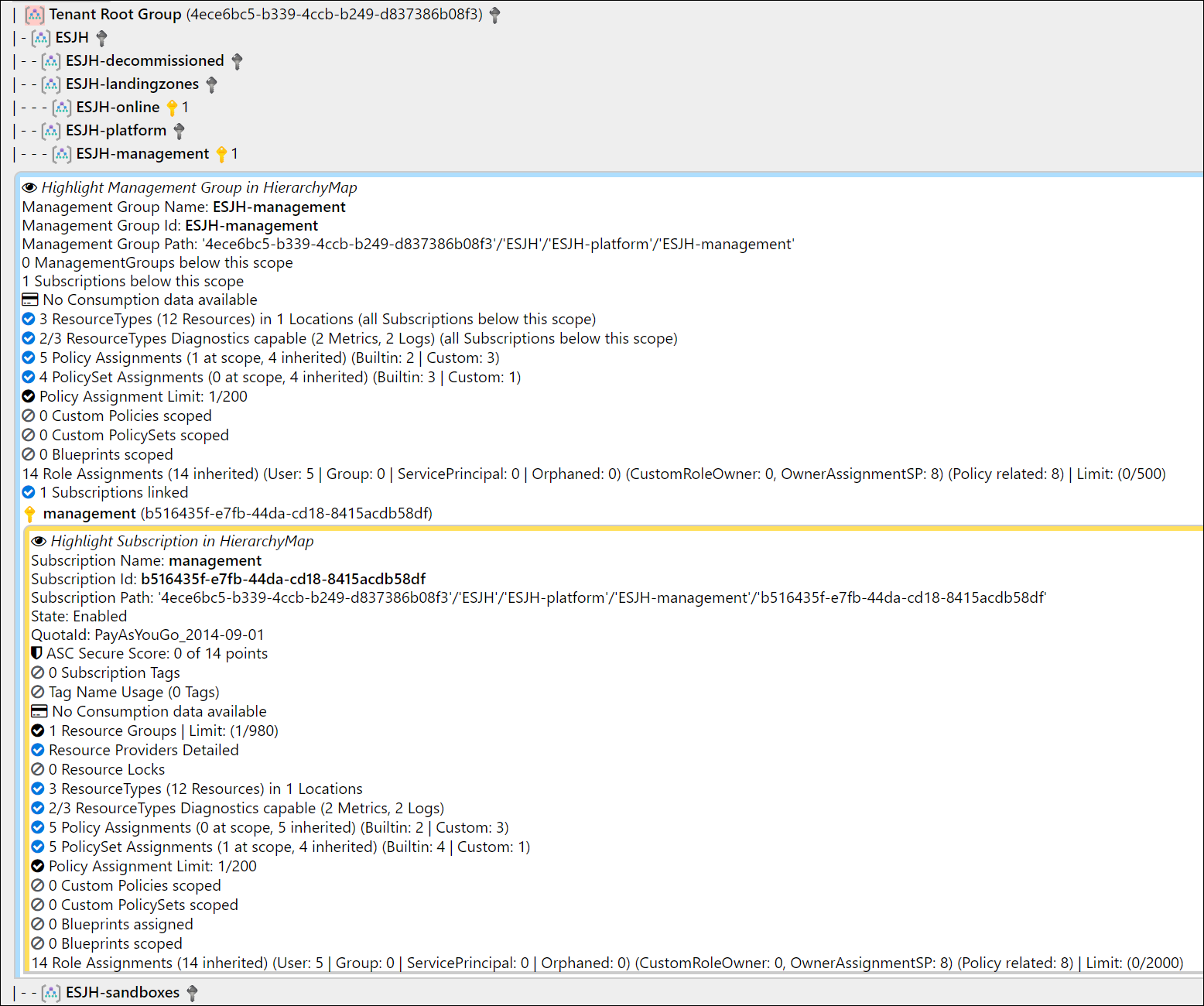
*IDs from screenshot are randomized
markdown in Azure DevOps Wiki as Code
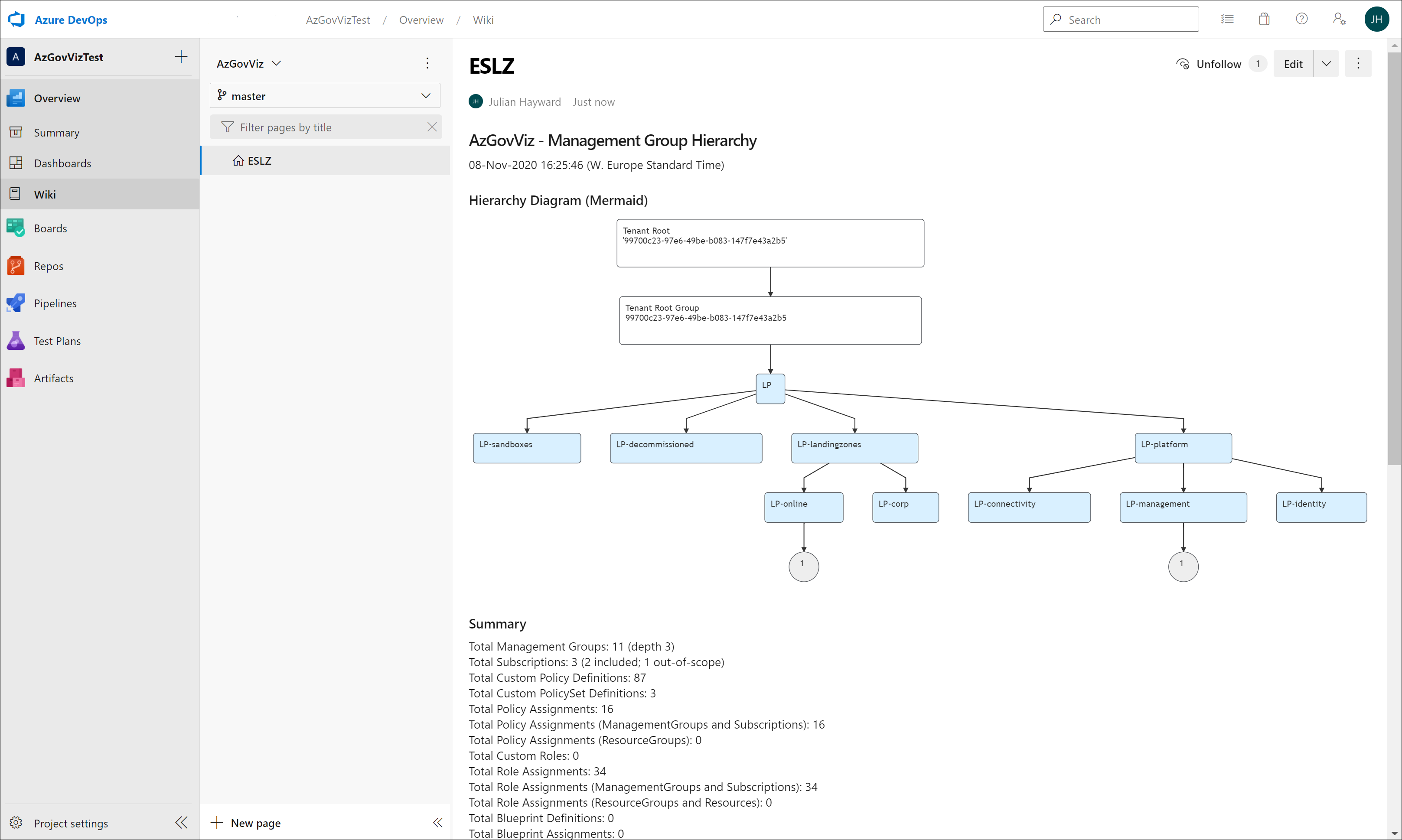 *IDs from screenshot are randomized
*IDs from screenshot are randomized
Outputs
- CSV file
- HTML file
- the HTML file uses Java Script and CSS files which are hosted on various CDNs (Content Delivery Network). For details review the BuildHTML region in the PowerShell script file.
- Browsers tested: Edge, new Edge and Chrome
- MD (Markdown) file
- for use with Azure DevOps Wiki leveraging the Mermaid plugin
Note: there is some fixing ongoing at the mermaid project to optimize the graphical experience:
https://github.com/mermaid-js/mermaid/issues/1177
AzGovViz slideset
Short presentation on AzGovViz Download
AzGovViz technical documentation
Required permissions in Azure
This permission is mandatory in each and every scenario!
| Scenario | Permissions |
|---|---|
| Console or AzureDevOps Pipeline | Reader Role assignment on Management Group level |
Required permissions in Azure Active Directory / API permissions
| Scenario | Permissions | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Console using a Guest user | Add to AAD Role Directory readers OR Use parameters: -NoAADGuestUsers -NoAADGroupsResolveMembers -NoAADServicePrincipalResolve |
|||||||||||||||
| Console using Service Principal |
Option 1 (simple setup but more read permissions than required) Add Service Principal to AAD Role Directory readers Option 2 (explicit permission model)
|
|||||||||||||||
| Azure DevOps Pipeline |
Option 1 (simple setup but more read permissions than required) Add Azure DevOps Service Connection's Service Principal to AAD Role Directory readers Option 2 (explicit permission model)
|
Usage
PowerShell
- Requires PowerShell Az Modules
- Az.Accounts
- Az.Resources
- Az.ResourceGraph
- Usage
.\AzGovVizParallel.ps1 -ManagementGroupId <your-Management-Group-Id>
- Parameters
-
-ManagementGroupIdTenant Id or any child Management Group Id -
-CsvDelimiterthe world is split into two kind of delimiters - comma and semicolon - choose yours -OutputPath-AzureDevOpsWikiAsCode-
-DoNotShowRoleAssignmentsUserDatascrub personally identifiable information (PII) -
-LimitCriticalPercentagelimit warning level, default is 80% -
-HierarchyTreeOnly-HierarchyMapOnlyoutput only the HierarchyMap for Management Groups including linked Subscriptions -
-SubscriptionQuotaIdWhitelistprocess only Subscriptions with defined QuotaId(s) -
-NoResourceProvidersDetaileddisables output for ResourceProvider states for all Subscriptions in the TenantSummary section, in large Tenants this can become time consuming -
-NoASCSecureScoredisables ASC Secure Score request for Subscriptions. The used API is in preview you may want to disable this -
-DisablePolicyComplianceStates-NoPolicyComplianceStateswill not query policy compliance states. You may want to use this parameter to accellerate script execution or when receiving error 'ResponseTooLarge'. -
-NoResourceDiagnosticsPolicyLifecycledisables Resource Diagnostics Policy Lifecycle recommendations -
-NoAADGroupsResolveMembersdisables resolving Azure Active Directory Group memberships -
-NoAADGuestUsersdisables resolving Azure Active Directory User type (Guest or Member) -
-NoServicePrincipalResolve-NoAADServicePrincipalResolvedisables resolving ServicePrincipals -
-ServicePrincipalExpiryWarningDays-AADServicePrincipalExpiryWarningDaysdefine warning period for Service Principal secret and certificate expiry; default is 14 days -
-NoAzureConsumptionAzure Consumption data should not be collected/reported -
-AzureConsumptionPerioddefine for which time period Azure Consumption data should be gathered; default is 1 day -
-NoAzureConsumptionReportExportToCSVAzure Consumption data should not be exported (CSV) -
-NoScopeInsights- Q: Why would you want to do this? A: In larger tenants the ScopeInsights section blows up the html file (up to unusable due to html file size) -
-ThrottleLimit- Leveraging PowerShell´s parallel capability you can define the ThrottleLimit (default=5) -
-DoTranscript- Log the console output -
-UseAzureRM
-
- Passed tests: Powershell Core 7.1.1 on Windows
Passed tests: Powershell 5.1.18362.752 on Windows- Passed tests: Powershell Core 7.1.1 Azure DevOps hosted ubuntu-18.04
Azure DevOps Pipeline
The provided example Pipeline is configured to run based on a schedule (every 12 hours). It will push the AzGovViz markdown output file to the 'wiki' folder in the 'Azure-MG-Sub-Governance-Reporting' Repository which will feed your Wiki.
- In Azure DevOps make sure to enable the Multistage Pipelines feature https://docs.microsoft.com/en-us/azure/devops/pipelines/get-started/multi-stage-pipelines-experience?view=azure-devops
- Clone the AzGovViz Repo
- Create Pipeline, configure your pipeline selecting Existing Azure Pipelines YAML file, select the AzGovViz YAML from the AzGovViz (Azure-MG-Sub-Governance-Reporting) Repo
- Grant Repository permissions: In order to allow the pipeline to push files back to our 'wiki' folder in the 'Azure-MG-Sub-Governance-Reporting' Repository the Build Service Account ('%ProjectName% Build Service (%OrgName%)') must be granted with Contribute permission
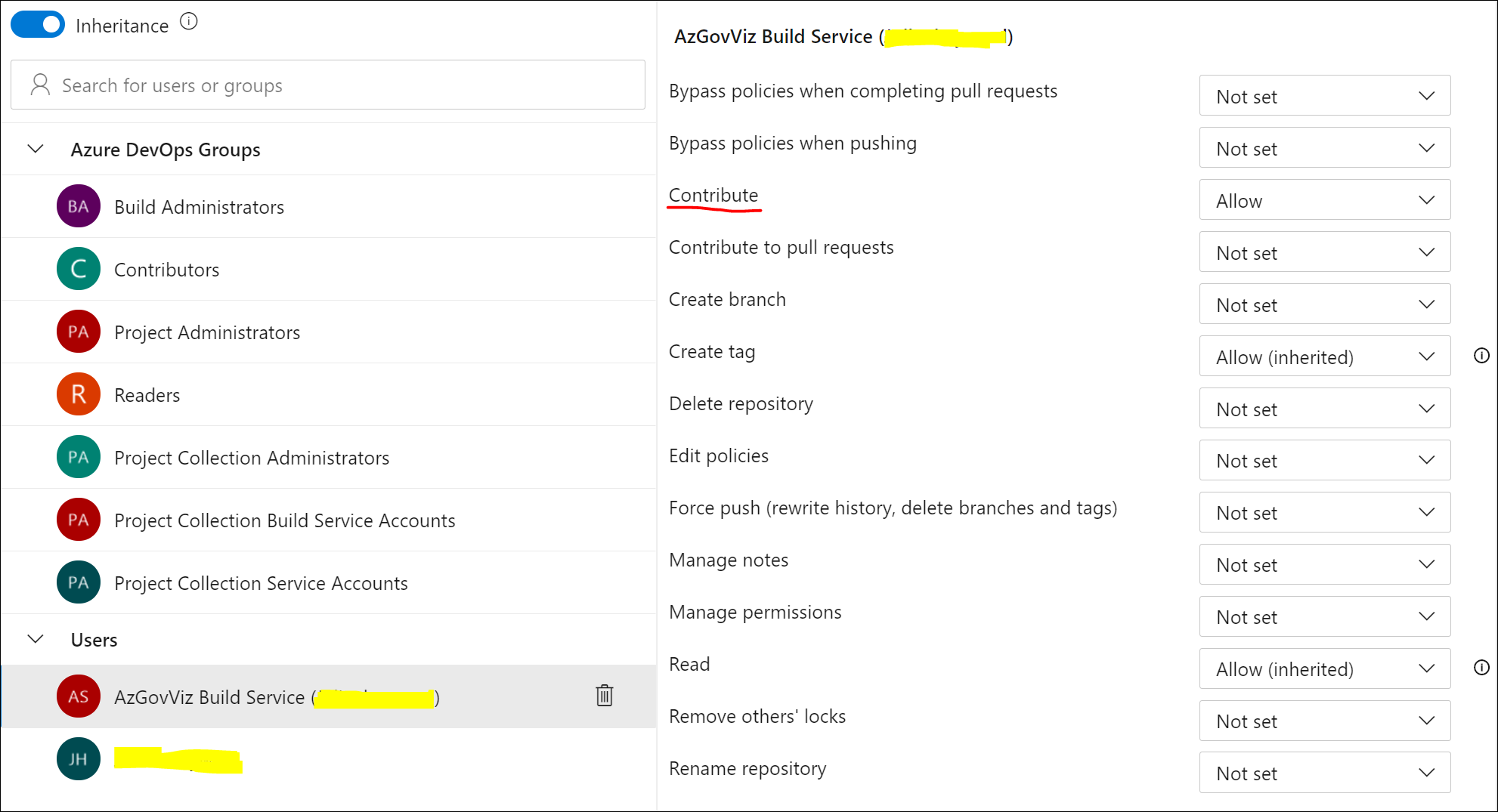
- Run the Pipeline
- Create Wiki by choosing Publish Code as Wiki, define the folder 'wiki' from the 'Azure-MG-Sub-Governance-Reporting' Repository as source
Make sure your Service Connection has the required permissions (see Required permissions in Azure).
AzGovViz sidenotes
Security
AzGovViz creates very detailed information about your Azure Governance setup. In your organization's best interest the outputs should be protected from not authorized access!
Facts
Disabled Subscriptions and Subscriptions where Quota Id starts with with "AAD_" are being skipped, all others are queried. More info on Quota Id / Offer numbers: Supported Microsoft Azure offers .
ARM Limits are not acquired programmatically, they are hardcoded. The links used to check related Limits are commented in the param section of the script.
Contributions
Please feel free to contribute. Thanks to so many supporters - testing, giving feedback, making suggestions, presenting use-case, posting/blogging articles, refactoring code - THANK YOU!
Thanks Stefan Stranger (Microsoft) for providing me with his AzGovViz outputs executed on his implementation of EnterpriseScale. Make sure you read Stefan´s Blog Article: Enterprise-Scale - Policy Driven Governance
Thanks Frank Oltmanns-Mack (Microsoft) for providing me with his AzGovViz outputs executed on his implementation of EnterpriseScale (see latest demo).
Special thanks to Tim Wanierke, Brooks Vaughn and Friedrich Weinmann (Microsoft).
Kudos to the TableFilter Project Team!
AzAdvertizer
Also check https://www.azadvertizer.net - AzAdvertizer helps you to keep up with the pace by providing overview and insights on new releases and changes/updates for Azure Governance capabilities such as Azure Policy's Policy definitions, initiatives (Set definitions), aliases and Azure RBAC's Role definitions and resource provider operations.
Final Note
Please note that while being developed by a Microsoft employee, AzGovViz is not a Microsoft service or product. AzGovViz is a personal/community driven project, there are none implicit or explicit obligations related to this project, it is provided 'as is' with no warranties and confer no rights.