sivasamyk / Logtrail
Licence: mit
Kibana plugin to view, search & live tail log events
Stars: ✭ 1,343
Programming Languages
javascript
184084 projects - #8 most used programming language
Projects that are alternatives of or similar to Logtrail
Docker Elastic
Deploy Elastic stack in a Docker Swarm cluster. Ship application logs and metrics using beats & GELF plugin to Elasticsearch
Stars: ✭ 202 (-84.96%)
Mutual labels: logstash, elasticsearch, logging, kibana
Elk Hole
elasticsearch, logstash and kibana configuration for pi-hole visualiziation
Stars: ✭ 136 (-89.87%)
Mutual labels: logstash, elasticsearch, logging, kibana
Json Logging Python
Python logging library to emit JSON log that can be easily indexed and searchable by logging infrastructure such as ELK, EFK, AWS Cloudwatch, GCP Stackdriver
Stars: ✭ 143 (-89.35%)
Mutual labels: logstash, elasticsearch, logging, kibana
Awesome Elasticsearch
A curated list of the most important and useful resources about elasticsearch: articles, videos, blogs, tips and tricks, use cases. All about Elasticsearch!
Stars: ✭ 4,168 (+210.35%)
Mutual labels: logstash, elasticsearch, kibana
Ansible Elk
📊 Ansible playbook for setting up an ELK/EFK stack and clients.
Stars: ✭ 284 (-78.85%)
Mutual labels: logstash, elasticsearch, kibana
Docker Elastic Stack
ELK Stack Dockerfile
Stars: ✭ 175 (-86.97%)
Mutual labels: logstash, elasticsearch, kibana
Docker Elk Tutorial
docker-elk-tutorial + django + logging
Stars: ✭ 69 (-94.86%)
Mutual labels: logstash, elasticsearch, kibana
Dynamite Nsm
DynamiteNSM is a free Network Security Monitor developed by Dynamite Analytics to enable network visibility and advanced cyber threat detection
Stars: ✭ 92 (-93.15%)
Mutual labels: logstash, elasticsearch, kibana
Helm Elasticstack
Kubernetes Helm Charts and Tools to run Elastic Stack(ELK) on Azure Container Service(AKS)
Stars: ✭ 76 (-94.34%)
Mutual labels: logstash, elasticsearch, kibana
synesis lite syslog
Syslog collection with the Elastic Stack.
Stars: ✭ 31 (-97.69%)
Mutual labels: kibana, logstash, syslog
Logstash
OSSEC + Logstash + Elasticsearch + Kibana
Stars: ✭ 74 (-94.49%)
Mutual labels: logstash, elasticsearch, kibana
Systemdlogger
Exports systemd logs to an external service, eg cloudwatch, elasticsearch
Stars: ✭ 91 (-93.22%)
Mutual labels: elasticsearch, logging, kibana
Elk Docker
Docker configuration for ELK monitoring stack with Curator and Beats data shippers support
Stars: ✭ 342 (-74.53%)
Mutual labels: logstash, elasticsearch, kibana
Elastiflow
Network flow analytics (Netflow, sFlow and IPFIX) with the Elastic Stack
Stars: ✭ 2,322 (+72.9%)
Mutual labels: logstash, elasticsearch, kibana
Justlog
JustLog brings logging on iOS to the next level. It supports console, file and remote Logstash logging via TCP socket with no effort. Support for logz.io available.
Stars: ✭ 439 (-67.31%)
Mutual labels: logstash, logging, kibana
Synesis lite suricata
Suricata IDS/IPS log analytics using the Elastic Stack.
Stars: ✭ 167 (-87.57%)
Mutual labels: logstash, elasticsearch, kibana
Microservices Sample
Sample project to create an application using microservices architecture
Stars: ✭ 167 (-87.57%)
Mutual labels: logstash, elasticsearch, kibana
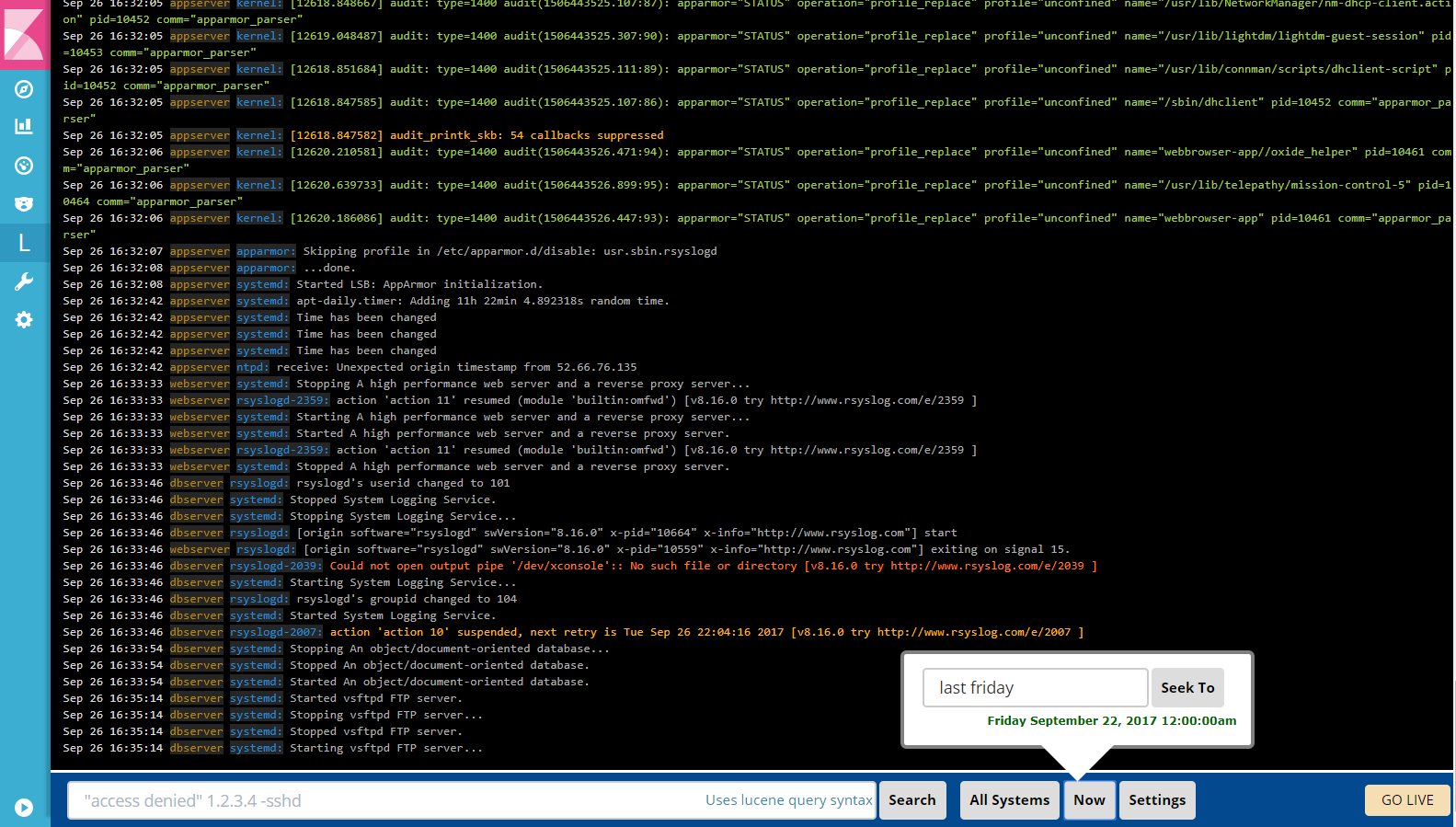
LogTrail - Log Viewer plugin for Kibana
LogTrail is a plugin for Kibana to view, analyze, search, and tail log events from multiple hosts in realtime with DevOps friendly interface inspired by Papertrail.
Features
- View, analyze, and search log events from a centralized interface
- Clean & simple DevOps friendly interface
- Live tail
- Filter aggregated logs by hosts and program
- Quickly seek to logs based on time
- Supports highlighting of search matches
- Supports multiple Elasticsearch index patterns each with different schemas
- Can be extended by adding additional fields to log event
- Color coding of messages based on field values
- Powerful search using Lucene query syntax
Installation
- Prerequisites
- Download and install Elasticsearch and Kibana
- Logtrail is supported and tested with Kibana 6.x and 5.x
- Install logtrail plugin (requires a restart of Kibana after install)
- Kibana 7.9.2 :
./bin/kibana-plugin install https://github.com/sivasamyk/logtrail/releases/download/v0.1.31/logtrail-7.9.2-0.1.31.zip - Kibana 5.6.5 :
./bin/kibana-plugin install https://github.com/sivasamyk/logtrail/releases/download/v0.1.23/logtrail-5.7.9.2.1.23.zip - Other versions : https://github.com/sivasamyk/logtrail/releases
- Kibana 7.9.2 :
- Kibana requires an exact match of the plugin version to the Kibana version. If you can't find the logtrail plugin release for a Kibana release, follow the instructions here to update the Kibana version in your logtrail plugin archive.
- Refer Logtrail Config Examples Repo for sample configurations for syslog, Java app, Kubernetes logs.
Configuration
- Logtrail can be configured by editing the following fields present in
logtrail.jsonfile located inside./plugins/logtraildirectory. -
default_index- Elasticsearch index where the syslog events are stored (default: logstash-*) -
default_time_range_in_days- Default time range in days to search when time is not specified using Seek button. Example: A value of 30 means logtrail will search only in logs from the last 30 days unless time is specified using the Seek button. A value of 0 means logtrail will search in all available logs by default. -
display_timezone- Timezone to display the timestamp in Event Viewer. e.g.America/Los_Angeles. The default value oflocalwill use the timezone of the browser. The time specified inSeek Topopup will always use browser timezone. -
display_timestamp_format- Format to display the timestamp in Event Viewer. For list of valid value refer here -
default_search- if specified, this will be applied as default search text while launching logtrail. The value can be any search text. e.g.ssh- shows all logs withsshin the message field. orlog_level:SEVERE- shows all logs wherelog_levelfield isSEVERE. The field name should be a valid field in the Elasticsearch document. The default search field is the field mapped tomessage. -
fields- Edit this parameter to map the event fields in ES to logtrail fields-
timestamp- maps to @timestamp field inserted by logstash. This will be used for querying internally. Logtrail recommends @timestamp to be stored in UTC in ES. -
hostname- hostname from where the events were received. Also used by hostname filter. The hostname field should be of typekeyword. For more info check out Hostname field need to be of type keyword -
program- program that generated this event. -
message- actual event message. This field will be used by search.
-
- Example: If the event fields names are @timestamp, host, process, message the mapping should be
"mapping" : {
"timestamp" : "@timestamp",
"hostname" : "host",
"program": "process",
"message": "message"
}
- By default each line displayed in the events view is of format:
display_timestamp hostname program:message -
message_format- Used to add additional fields to be shown for log event. For more details refer Adding additional fields -
keyword_suffix- Specifies the keyword suffix to be appended for hostname & program fields. Set it to empty string ("") to not append any suffix. If not specified (undefined) logtrail will appendkeyword. -
color_mapping- Color code messages based on field values. For more details refer Color coding messages - Any changes in
logtrail.jsonrequire a restart of Kibana - Logtrail can read
logtrail.jsonconfiguration from Elasticsearch instead of the filesystem. This will be useful when sharing the same configuration across multiple installations. For more info refer Load Logtrail configuration from Elasticsearch - Refer logtrail-config-examples repo for sample configurations
- Logs & Events from Windows, Java, Python, PHP, Perl, Ruby, Android, Docker, .Net can be shipped using the syslog protocol.
- For more configuration options refer to Papertrail Configuration Help.
- Beats/Fluentd can also be used to ship events to ES and fields can be mapped using the
fieldsparameter inlogtrail.json
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].