sadsfae / Ansible Elk
Licence: apache-2.0
📊 Ansible playbook for setting up an ELK/EFK stack and clients.
Stars: ✭ 284
Programming Languages
shell
77523 projects
Projects that are alternatives of or similar to Ansible Elk
Spring Boot Microservice Eureka Zuul Docker
Spring-Boot rest microservices using Eureka, Zuul, Docker. Monitoring with logstash, logback, elasticsearch, kibana
Stars: ✭ 45 (-84.15%)
Mutual labels: logstash, elk, elasticsearch, kibana
Ansible Elk Playbook
A playbook for setting up the ELK Stack + beats log shippers on Ubuntu 16.04 and above
Stars: ✭ 83 (-70.77%)
Mutual labels: ansible, elk, playbook, kibana
Elastic
Elastic Stack (6.2.4) 을 활용한 Dashboard 만들기 Project
Stars: ✭ 121 (-57.39%)
Mutual labels: logstash, elk, elasticsearch, kibana
Elk Docker
Docker configuration for ELK monitoring stack with Curator and Beats data shippers support
Stars: ✭ 342 (+20.42%)
Mutual labels: logstash, elk, elasticsearch, kibana
Elastiflow
Network flow analytics (Netflow, sFlow and IPFIX) with the Elastic Stack
Stars: ✭ 2,322 (+717.61%)
Mutual labels: logstash, elk, elasticsearch, kibana
Docker monitoring logging alerting
Docker host and container monitoring, logging and alerting out of the box using cAdvisor, Prometheus, Grafana for monitoring, Elasticsearch, Kibana and Logstash for logging and elastalert and Alertmanager for alerting.
Stars: ✭ 479 (+68.66%)
Mutual labels: logstash, elk, elasticsearch, kibana
Json Logging Python
Python logging library to emit JSON log that can be easily indexed and searchable by logging infrastructure such as ELK, EFK, AWS Cloudwatch, GCP Stackdriver
Stars: ✭ 143 (-49.65%)
Mutual labels: logstash, elk, elasticsearch, kibana
Docker Elk
The Elastic stack (ELK) powered by Docker and Compose.
Stars: ✭ 12,327 (+4240.49%)
Mutual labels: logstash, elk, elasticsearch, kibana
Synesis lite suricata
Suricata IDS/IPS log analytics using the Elastic Stack.
Stars: ✭ 167 (-41.2%)
Mutual labels: logstash, elk, elasticsearch, kibana
Elk Docker
Elasticsearch, Logstash, Kibana (ELK) Docker image
Stars: ✭ 1,973 (+594.72%)
Mutual labels: logstash, elk, elasticsearch, kibana
Vagrant Elastic Stack
Giving the Elastic Stack a try in Vagrant
Stars: ✭ 131 (-53.87%)
Mutual labels: ansible, logstash, elasticsearch, kibana
Kubeadm Playbook
Fully fledged (HA) Kubernetes Cluster using official kubeadm, ansible and helm. Tested on RHEL/CentOS/Ubuntu with support of http_proxy, dashboard installed, ingress controller, heapster - using official helm charts
Stars: ✭ 533 (+87.68%)
Mutual labels: ansible, playbook, centos, rhel
Terraform Aws Elasticsearch
Terraform module to provision an Elasticsearch cluster with built-in integrations with Kibana and Logstash.
Stars: ✭ 137 (-51.76%)
Mutual labels: elk, elasticsearch, fluentd, kibana
Elk Stack
ELK Stack ... based on Elastic Stack 5.x
Stars: ✭ 148 (-47.89%)
Mutual labels: logstash, elk, elasticsearch, kibana
Pfelk
pfSense/OPNsense + ELK
Stars: ✭ 417 (+46.83%)
Mutual labels: ansible, logstash, elasticsearch, kibana
Mattermost Ansible
Ansible playbook to provide a turnkey solution for the Team Edition of Mattermost
Stars: ✭ 126 (-55.63%)
Mutual labels: ansible, playbook, centos
Ansible Role Logstash
Ansible Role - Logstash
Stars: ✭ 136 (-52.11%)
Mutual labels: ansible, logstash, elk
tsharkVM
tshark + ELK analytics virtual machine
Stars: ✭ 51 (-82.04%)
Mutual labels: kibana, logstash, elk
ansible-elk
Ansible Playbook for setting up the ELK/EFK Stack and Filebeat client on remote hosts
What does it do?
- Automated deployment of a full 6.x series ELK or EFK stack (Elasticsearch, Logstash/Fluentd, Kibana)
-
5.6and2.4ELK versions are maintained as branches andmasterbranch will be 6.x currently. - Uses Nginx as a reverse proxy for Kibana, or optionally Apache via
apache_reverse_proxy: true - Generates SSL certificates for Filebeat or Logstash-forwarder
- Adds either iptables or firewalld rules if firewall is active
- Tunes Elasticsearch heapsize to half your memory, to a max of 32G
- Deploys ELK clients using SSL and Filebeat for Logstash (Default)
- Deploys rsyslog if Fluentd is chosen over Logstash, picks up the same set of OpenStack-related logs in /var/log/*
- All service ports can be modified in
install/group_vars/all.yml - Optionally install curator
- Optionally install Elastic X-Pack Suite
- This is also available on Ansible Galaxy
-
Requirements
- RHEL7 or CentOS7 server/client with no modifications
- RHEL7/CentOS7 or Fedora for ELK clients using Filebeat
- ELK/EFK server with at least 8G of memory (you can try with less but 5.x series is quite demanding - try 2.4 series if you have scarce resources).
- You may want to modify
vm.swappinessas ELK/EFK is demanding and swapping kills the responsiveness.- I am leaving this up to your judgement.
echo "vm.swappiness=10" >> /etc/sysctl.conf
sysctl -p
Notes
- Current ELK version is 6.x but you can checkout the 5.6 or 2.4 branch if you want that series
- I will update this playbook for major ELK versions going forward as time allows.
- Sets the nginx htpasswd to admin/admin initially
- nginx ports default to 80/8080 for Kibana and SSL cert retrieval (configurable)
- Uses OpenJDK for Java
- It's fairly quick, takes around 3minutes on a test VM
- Fluentd can be substituted for the default Logstash
- Set
logging_backend: fluentdingroup_vars/all.yml
- Set
- Install curator by setting
install_curator_tool: trueininstall/group_vars/all.yml - Install Elastic X-Pack Suite for Elasticsearch, LogStash or Kibana via:
install_elasticsearch_xpack: trueinstall_kibana_xpack: trueinstall_logstash_xpack: true- Note: Deploying X-Pack will wrap your ES with additional authentication and security, Kibana for example will have it's own credentials now - the default is username:
elasticand password:changeme
ELK/EFK Server Instructions
- Clone repo and setup your hosts file
git clone https://github.com/sadsfae/ansible-elk
cd ansible-elk
sed -i 's/host-01/elkserver/' hosts
sed -i 's/host-02/elkclient/' hosts
- If you're using a non-root user for Ansible, e.g. AWS EC2 likes to use ec2-user then set the follow below, default is root.
ansible_system_user: ec2-user
- Run the playbook
ansible-playbook -i hosts install/elk.yml
- (see playbook messages)
- Navigate to the ELK at http://host-01:80 (default, nginx) or http://host-01/kibana (apache)
- Default login is:
- username:
admin - password:
admin
- username:
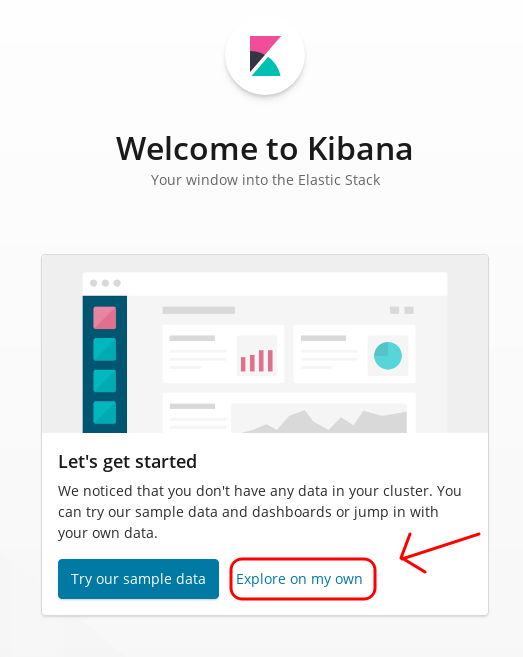
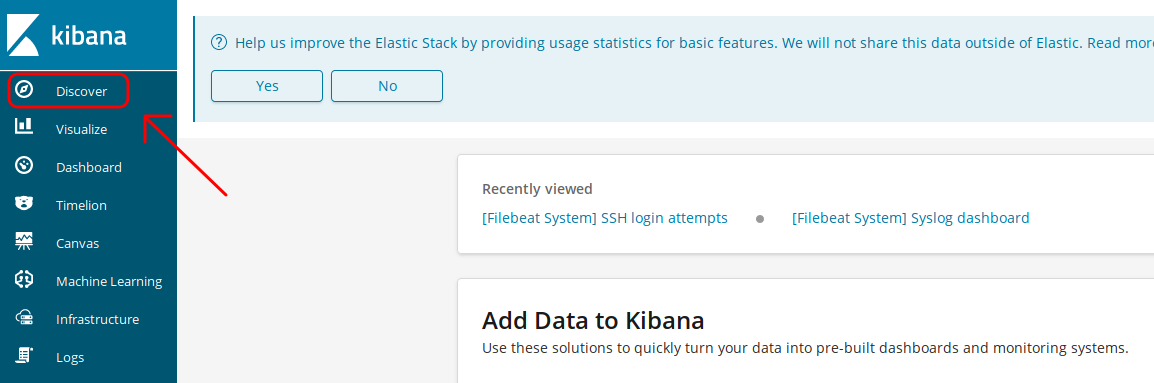
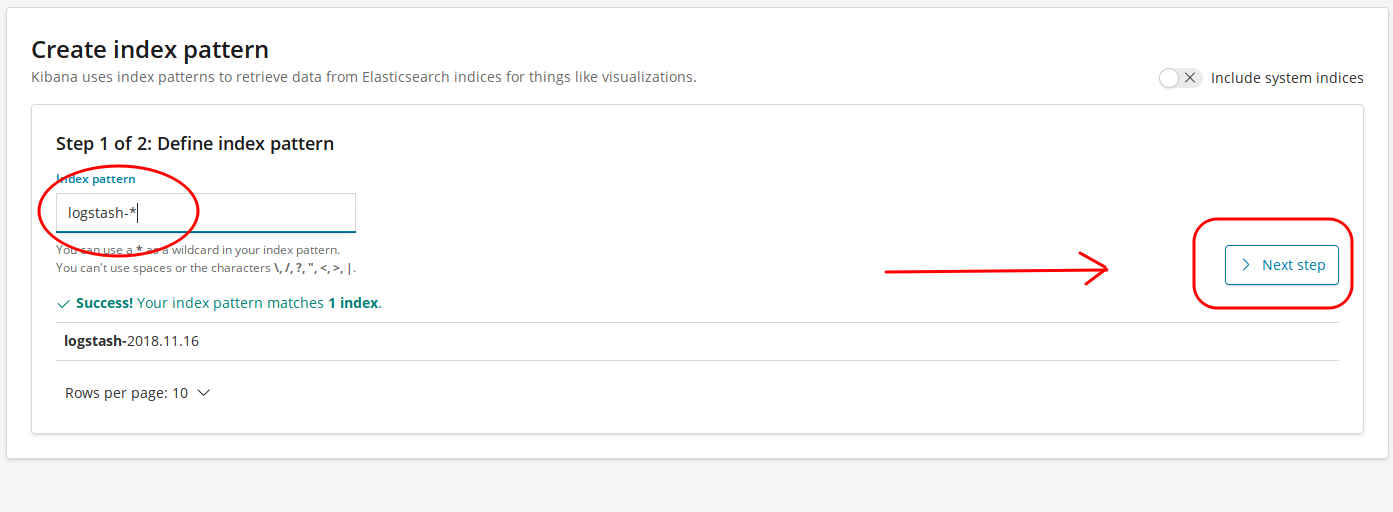
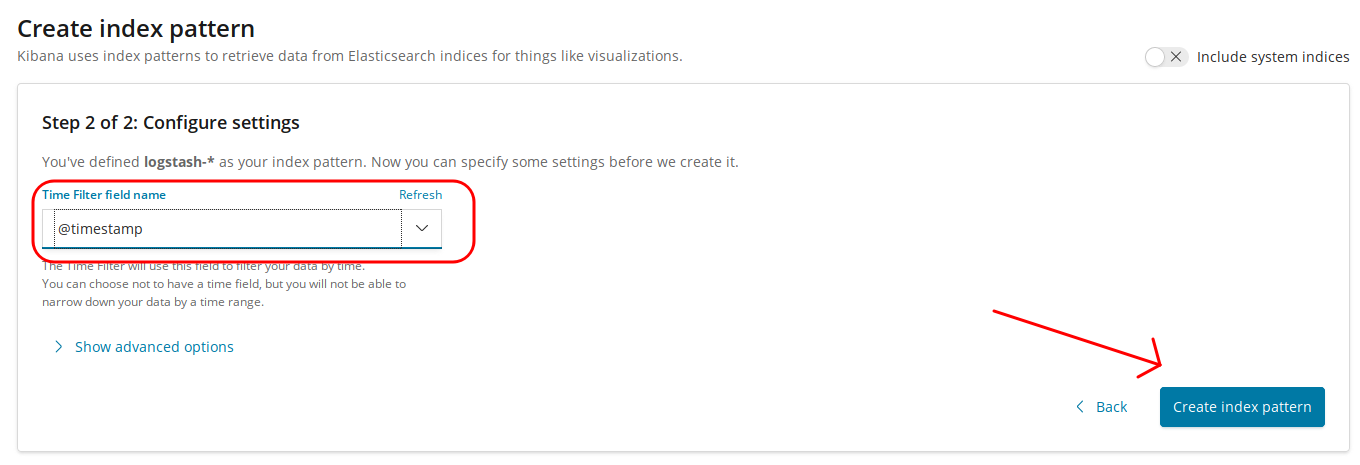
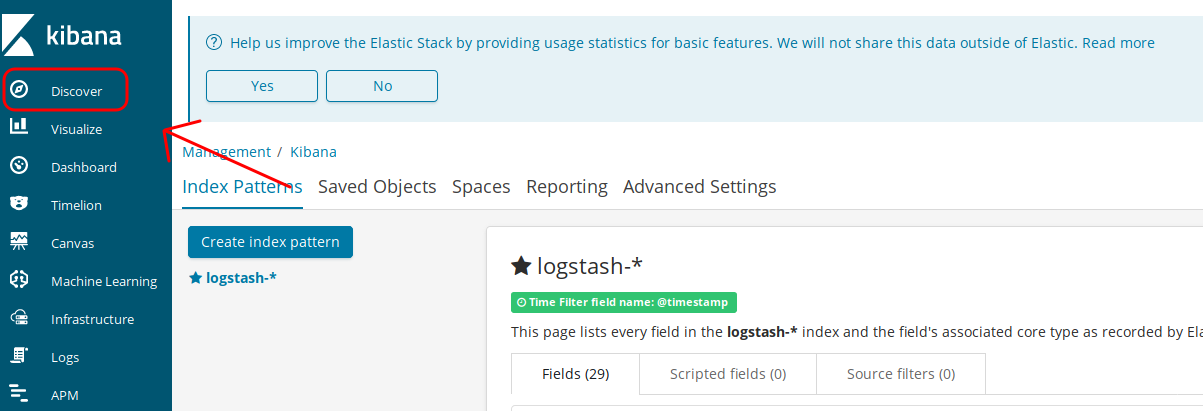
Create your Kibana Index Pattern
- Next you'll login to your Kibana instance and create a Kibana index pattern.
- Note: Sample data can be useful, you can try it later however.
- At this point you can setup your client(s) to start sending data via Filebeat/SSL
ELK Client Instructions
- Run the client playbook against the generated
elk_servervariable
ansible-playbook -i hosts install/elk-client.yml --extra-vars 'elk_server=X.X.X.X'
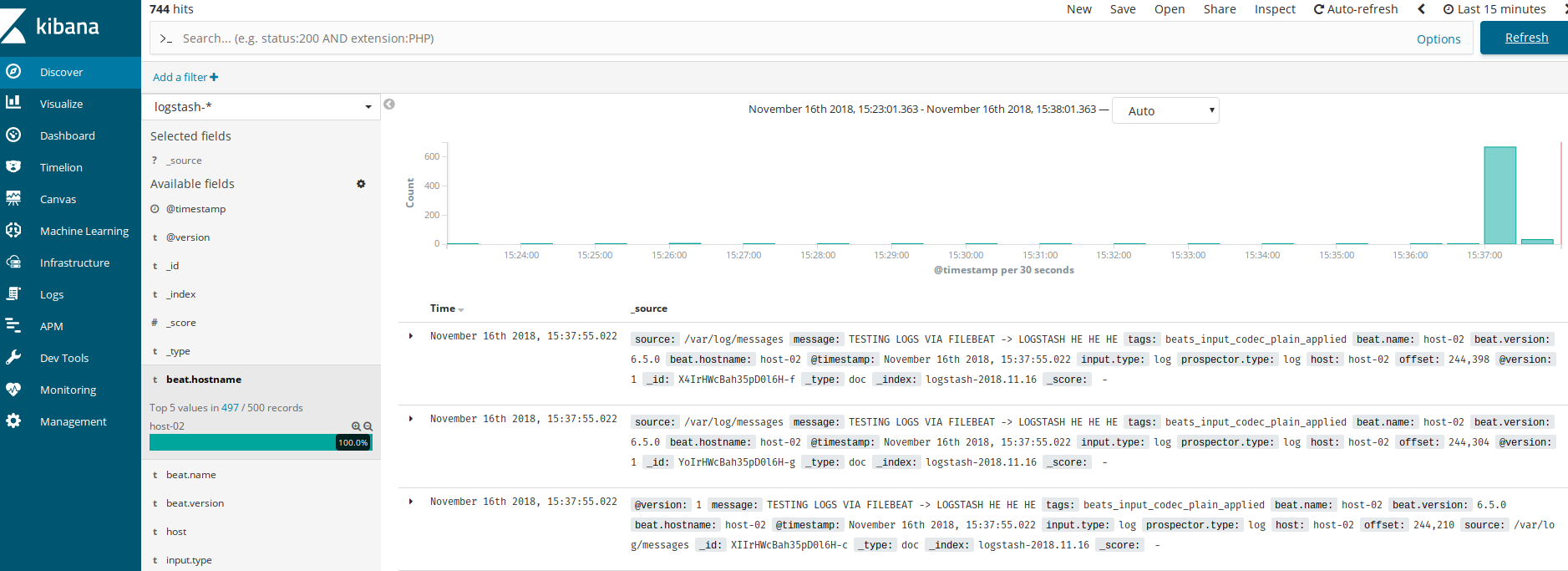
- Once this completes return to your ELK and you'll see log results come in from ELK/EFK clients via filebeat
5.6 ELK/EFK (Deprecated)
- The 5.6 series of ELK/EFK is also available, to use this just use the 5.6 branch
git clone https://github.com/sadsfae/ansible-elk
cd ansible-elk
git checkout 5.6
2.4 ELK/EFK (Deprecated)
- The 2.4 series of ELK/EFK is also available, to use this just use the 2.4 branch
git clone https://github.com/sadsfae/ansible-elk
cd ansible-elk
git checkout 2.4
- You can view a deployment video here:
File Hierarchy
.
├── hosts
├── install
│ ├── elk_client.yml
│ ├── elk.yml
│ ├── group_vars
│ │ └── all.yml
│ └── roles
│ ├── apache
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ ├── 8080vhost.conf.j2
│ │ └── kibana.conf.j2
│ ├── curator
│ │ ├── files
│ │ │ └── curator.repo
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ ├── curator-action.yml.j2
│ │ └── curator-config.yml.j2
│ ├── elasticsearch
│ │ ├── files
│ │ │ ├── elasticsearch.in.sh
│ │ │ └── elasticsearch.repo
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ └── elasticsearch.yml.j2
│ ├── elk_client
│ │ ├── files
│ │ │ └── elk.repo
│ │ └── tasks
│ │ └── main.yml
│ ├── filebeat
│ │ ├── meta
│ │ │ └── main.yml
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ ├── filebeat.yml.j2
│ │ └── rsyslog-openstack.conf.j2
│ ├── firewall
│ │ ├── handlers
│ │ │ └── main.yml
│ │ └── tasks
│ │ └── main.yml
│ ├── fluentd
│ │ ├── files
│ │ │ ├── filebeat-index-template.json
│ │ │ └── fluentd.repo
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ ├── openssl_extras.cnf.j2
│ │ └── td-agent.conf.j2
│ ├── heartbeat
│ │ ├── meta
│ │ │ └── main.yml
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ └── heartbeat.yml.j2
│ ├── instructions
│ │ └── tasks
│ │ └── main.yml
│ ├── kibana
│ │ ├── files
│ │ │ └── kibana.repo
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ └── kibana.yml.j2
│ ├── logstash
│ │ ├── files
│ │ │ ├── filebeat-index-template.json
│ │ │ └── logstash.repo
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ ├── 02-beats-input.conf.j2
│ │ ├── logstash.conf.j2
│ │ └── openssl_extras.cnf.j2
│ ├── metricbeat
│ │ ├── meta
│ │ │ └── main.yml
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ └── metricbeat.yml.j2
│ ├── nginx
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ ├── kibana.conf.j2
│ │ └── nginx.conf.j2
│ ├── packetbeat
│ │ ├── meta
│ │ │ └── main.yml
│ │ ├── tasks
│ │ │ └── main.yml
│ │ └── templates
│ │ └── packetbeat.yml.j2
│ └── xpack
│ └── tasks
│ └── main.yml
└── meta
└── main.yml
56 directories, 52 files
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].