nyxgeek / Ntlmscan
scan for NTLM directories
Stars: ✭ 141
Programming Languages
python
139335 projects - #7 most used programming language
Projects that are alternatives of or similar to Ntlmscan
Whatweb
Next generation web scanner
Stars: ✭ 3,503 (+2384.4%)
Mutual labels: hacking, scanner, pentest
Xspear
Powerfull XSS Scanning and Parameter analysis tool&gem
Stars: ✭ 583 (+313.48%)
Mutual labels: hacking, scanner, pentest
Ladon
大型内网渗透扫描器&Cobalt Strike,Ladon8.9内置120个模块,包含信息收集/存活主机/端口扫描/服务识别/密码爆破/漏洞检测/漏洞利用。漏洞检测含MS17010/SMBGhost/Weblogic/ActiveMQ/Tomcat/Struts2,密码口令爆破(Mysql/Oracle/MSSQL)/FTP/SSH(Linux)/VNC/Windows(IPC/WMI/SMB/Netbios/LDAP/SmbHash/WmiHash/Winrm),远程执行命令(smbexec/wmiexe/psexec/atexec/sshexec/webshell),降权提权Runas、GetSystem,Poc/Exploit,支持Cobalt Strike 3.X-4.0
Stars: ✭ 2,911 (+1964.54%)
Mutual labels: hacking, scanner, pentest
Reconspider
🔎 Most Advanced Open Source Intelligence (OSINT) Framework for scanning IP Address, Emails, Websites, Organizations.
Stars: ✭ 621 (+340.43%)
Mutual labels: hacking, scanner, pentest
K8cscan
K8Cscan大型内网渗透自定义插件化扫描神器,包含信息收集、网络资产、漏洞扫描、密码爆破、漏洞利用,程序采用多线程批量扫描大型内网多个IP段C段主机,目前插件包含: C段旁注扫描、子域名扫描、Ftp密码爆破、Mysql密码爆破、Oracle密码爆破、MSSQL密码爆破、Windows/Linux系统密码爆破、存活主机扫描、端口扫描、Web信息探测、操作系统版本探测、Cisco思科设备扫描等,支持调用任意外部程序或脚本,支持Cobalt Strike联动
Stars: ✭ 693 (+391.49%)
Mutual labels: hacking, scanner, pentest
Reconftw
reconFTW is a tool designed to perform automated recon on a target domain by running the best set of tools to perform scanning and finding out vulnerabilities
Stars: ✭ 974 (+590.78%)
Mutual labels: hacking, scanner, pentest
K8tools
K8工具合集(内网渗透/提权工具/远程溢出/漏洞利用/扫描工具/密码破解/免杀工具/Exploit/APT/0day/Shellcode/Payload/priviledge/BypassUAC/OverFlow/WebShell/PenTest) Web GetShell Exploit(Struts2/Zimbra/Weblogic/Tomcat/Apache/Jboss/DotNetNuke/zabbix)
Stars: ✭ 4,173 (+2859.57%)
Mutual labels: hacking, scanner, pentest
Jok3r
Jok3r v3 BETA 2 - Network and Web Pentest Automation Framework
Stars: ✭ 645 (+357.45%)
Mutual labels: hacking, scanner, pentest
Pidrila
Python Interactive Deepweb-oriented Rapid Intelligent Link Analyzer
Stars: ✭ 125 (-11.35%)
Mutual labels: hacking, scanner, pentest
Xattacker
X Attacker Tool ☣ Website Vulnerability Scanner & Auto Exploiter
Stars: ✭ 897 (+536.17%)
Mutual labels: hacking, scanner, pentest
Webhackersweapons
⚔️ Web Hacker's Weapons / A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting
Stars: ✭ 1,205 (+754.61%)
Mutual labels: hacking, scanner
Cloudfail
Utilize misconfigured DNS and old database records to find hidden IP's behind the CloudFlare network
Stars: ✭ 1,239 (+778.72%)
Mutual labels: scanner, pentest
Web Brutator
Fast Modular Web Interfaces Bruteforcer
Stars: ✭ 97 (-31.21%)
Mutual labels: hacking, pentest
Burp Bounty Profiles
Burp Bounty profiles compilation, feel free to contribute!
Stars: ✭ 76 (-46.1%)
Mutual labels: hacking, pentest
Cve 2019 0604
cve-2019-0604 SharePoint RCE exploit
Stars: ✭ 91 (-35.46%)
Mutual labels: hacking, pentest
Keye
Keye is a reconnaissance tool that was written in Python with SQLite3 integrated. After adding a single URL, or a list of URLs, it will make a request to these URLs and try to detect changes based on their response's body length.
Stars: ✭ 101 (-28.37%)
Mutual labels: hacking, pentest
Hacker Container
Container with all the list of useful tools/commands while hacking and pentesting Kubernetes Clusters
Stars: ✭ 105 (-25.53%)
Mutual labels: hacking, pentest
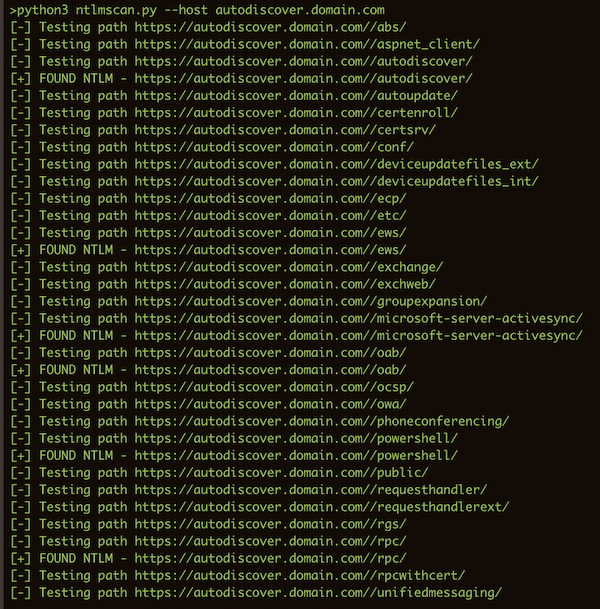
ntlmscan
scan for NTLM directories
reliable targets are:
- OWA servers
- Skype for Business/Lync servers
- Autodiscover servers (autodiscover.domain.com and lyncdiscover.domain.com)
- ADFS servers
once identified, use nmap and the http-ntlm-info script to extract internal domain/server information
usage: ntlmscan.py [-h] [--url URL] [--host HOST] [--hostfile HOSTFILE]
[--outfile OUTFILE] [--dictionary DICTIONARY]
optional arguments:
-h, --help show this help message and exit
--url URL full url path to test
--host HOST a single host to search for ntlm dirs on
--hostfile HOSTFILE file containing ips or hostnames to test
--outfile OUTFILE file to write results to
--dictionary DICTIONARY list of paths to test, default: paths.dict
--nmap run nmap with http-ntlm-info after testing (requires nmap)
--debug show request headers
Examples:
python3 ntlmscan.py --url https://autodiscover.domain.com/autodiscover
python3 ntlmscan.py --host autodiscover.domain.com
python3 ntlmscan.py --hostfile hosts.txt --dictionary big.txt
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].