GoogleCloudPlatform / Pci Gke Blueprint
Projects that are alternatives of or similar to Pci Gke Blueprint
PCI on GKE Blueprint
This is the companion repository to the PCI on GKE Security Blueprint for the Google Cloud Platform. It contains a set of Terraform configurations and scripts to help demonstrate how to bootstrap a PCI environment in GCP. When appropriate, we also showcase GCP services, tools, or projects we think might be useful to start your own GCP PCI environment or as samples for any other purposes.
Here are the projects/services we make use of in this Blueprint:
- Terraform
- Helm
- Google Kubernetes Engine (GKE)
- Istio
- Cloud Armor
- Google-managed SSL Certificates
- GoogleCloudPlatform/microservices-demo
Documentation
- Quickstart
- Prerequisites
- Workstation Configuration
- Building the Infrastructure
- Deploying the Application
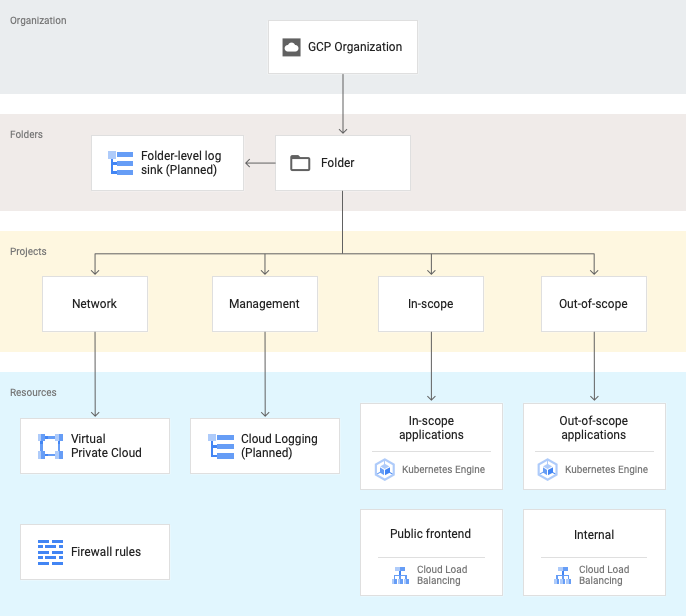
- Diagrams
- Kubernetes RBAC via Google Groups membership demonstration
- Development
- Continuous Integration with Cloud Build
- Known Issues and Limitations
- Helpful Links
Quickstart
We recommend you read through the documentation in Building the Infrastructure and Deploying the Application but if you just want to get started:
- Follow the steps in Prerequisites
- Set-up the workstation.env file Workstation Configuration
- Run
./_helpers/build-infra.sh - Run
./_helpers/deploy-app.sh
Prerequisites
Before starting, we need to make sure that our local environment is configured correctly. We need to make sure we have the correct tools and a GCP account with the correct permissions.
Installation Dependencies
GCP IAM Requirements
In order to execute this module you will need access to a Google Cloud Organization, with Organization Admin and Folder Admin permissions.
Authenticate to gcloud
- Once the gcloud SDK is installed, run gcloud auth login to authenticate with your Google Account.
Workstation Configuration
This project comes with a workstation.env.example file that is intended to be copied and customized for your environment.
cp workstation.env.example workstation.env
You can find the values for YOUR_ORG_ID and YOUR_BILLING_ACCOUNT_ID using the following commands:
gcloud organizations list
gcloud beta billing accounts list
To create a folder follow these instructions.
Most variables can be left as-is, this is a list of the ones that are required to be set, see the comments in-line for details:
TF_VAR_org_idTF_VAR_gsuite_idTF_VAR_billing_accountTF_VAR_folder_idTF_ADMIN_BUCKETTF_VAR_frontend_zone_dns_nameGOOGLE_GROUPS_DOMAINSRC_PATHREPOSITORY_NAME
You'll need to source your workstaion.env file before executing any of the steps in this Blueprint:
source workstation.env
- At this point, your workstation is ready. Continue from here by either running
./_helpers/build-infra.sh, or following the stepwise instructions for that script in Building the Infrastructure.
Known Issues and Limitations
- If your GCP Organization is shared between other users or teams, consult your Organization Admins before building the Blueprint.
- This Blueprint does not implement a multi-environment setup. There is no "pre-prod", "staging", or "production" differentiation. However, there is no reason that this Blueprint couldn't be expanded to accommodate such a setup if you so choose.
- This Blueprint is meant to showcase various GCP features and act as a starting point to build a security-focused environment focused on PCI compliance. This Blueprint has been reviewed by Coalfire but deploying an application into this environment does not qualify as being PCI-DSS compliant.
- As currently designed,
http://requests are redirected tohttps://via HTTP header inspection by the frontend microservice. More details in HTTP to HTTPS redirection
Helpful Links
- Significant portions of this project are based on "Building a multi-cluster service mesh on GKE using replicated control-plane architecture"