petoolse / Petools
Licence: mit
PE Tools - Portable executable (PE) manipulation toolkit
Stars: ✭ 528
Projects that are alternatives of or similar to Petools
SDA
SDA is a rich cross-platform tool for reverse engineering that focused firstly on analysis of computer games. I'm trying to create a mix of the Ghidra, Cheat Engine and x64dbg. My tool will combine static and dynamic analysis of programs. Now SDA is being developed.
Stars: ✭ 98 (-81.44%)
Mutual labels: analysis, disassembler
Gtirb
Intermediate Representation for Binary analysis and transformation
Stars: ✭ 190 (-64.02%)
Mutual labels: analysis, disassembler
Awesome Express
A curated list of awesome express.js resources
Stars: ✭ 456 (-13.64%)
Mutual labels: resources
Ffmpegcore
A .NET FFMpeg/FFProbe wrapper for easily integrating media analysis and conversion into your C# applications
Stars: ✭ 429 (-18.75%)
Mutual labels: analysis
Console Importer
Easily import JS and CSS resources from Chrome console.
Stars: ✭ 426 (-19.32%)
Mutual labels: resources
Elm Analyse
A tool that allows you to analyse your Elm code, identify deficiencies and apply best practices.
Stars: ✭ 418 (-20.83%)
Mutual labels: analysis
Dexcalibur
[Official] Android reverse engineering tool focused on dynamic instrumentation automation. Powered by Frida. It disassembles dex, analyzes it statically, generates hooks, discovers reflected methods, stores intercepted data and does new things from it. Its aim is to be an all-in-one Android reverse engineering platform.
Stars: ✭ 512 (-3.03%)
Mutual labels: analysis
Fieldtrip
The MATLAB toolbox for MEG, EEG and iEEG analysis
Stars: ✭ 481 (-8.9%)
Mutual labels: analysis
Awesome Writing
An awesome list of information to help developers write better, kinder, more helpful documentation and learning materials
Stars: ✭ 462 (-12.5%)
Mutual labels: resources
Graphql Query Complexity
GraphQL query complexity analysis and validation for graphql-js
Stars: ✭ 424 (-19.7%)
Mutual labels: analysis
Deep Learning Roadmap
📡 All You Need to Know About Deep Learning - A kick-starter
Stars: ✭ 4,225 (+700.19%)
Mutual labels: resources
Flutter Rehberi
Flutter için Türkçe ve İngilizce kaynakların toplandığı rehber
Stars: ✭ 444 (-15.91%)
Mutual labels: resources
Rz Ghidra
Deep ghidra decompiler and sleigh disassembler integration for rizin
Stars: ✭ 478 (-9.47%)
Mutual labels: disassembler
Distributed Systems Technologies And Cases Analysis
《分布式系统常用技术及案例分析》示例源码
Stars: ✭ 446 (-15.53%)
Mutual labels: analysis
Sympact
🔥 Stupid Simple CPU/MEM "Profiler" for your JS code.
Stars: ✭ 439 (-16.86%)
Mutual labels: resources
PE Tools - portable executable (PE) manipulation toolkit.
Table of contents
Description
PE Tools lets you actively research PE files and processes.
Process Viewerand PE filesEditor,Dumper,Rebuilder,Comparator,Analyzerare included. PE Tools is an oldschool reverse engineering tool with a long history since2002. PE Tools was initially inspired by LordPE (yoda).
Features
PE Editor
- PE and DOS Headers Editor
- PE Sections Editor
- PE Directory Viewer and Editor
- Export Directory Editor
- Import Directory Editor
- Resource Directory Viewer
- Exception Directory Viewer
- Relocation Directory Viewer
- Debug Directory Viewer
- TLS Directory Editor
- Load Config Directory Editor
- Bound Directory Editor
File Location Calculator (FLC)
- Virtual Address
- Relative Virtual Address
- Raw File Offset
PE Files Comparator
- Side-by-side comparison of headers and characteristics of two PE files
Process Viewer and Manager
- Show basic process information
- Show process modules
PE Dumper
- Running process dumper
- Full Dump
- Partial Dump
- Region Dump
Dumper Server (accessible via Dumper Server SDK)
PE Rebuilder
- Dump Fixer
- Relocation Wiper
- Resource Directory Rebuilder
- PE file Validation
- Imports Binder
- ImageBase Changer
PE Sniffer
- Signature analysis of PE files
- Packer detection
HEX Editor
- HEX Editor available in:
-
Section Editorvia section context menu - Every
Data DirectoryinDirectory Editor
-
Plugins
PE ToolsPlugin SDKavailable
What's new in recent major releases
PE Tools v1.9
Complete PE Tools v1.9 announces:
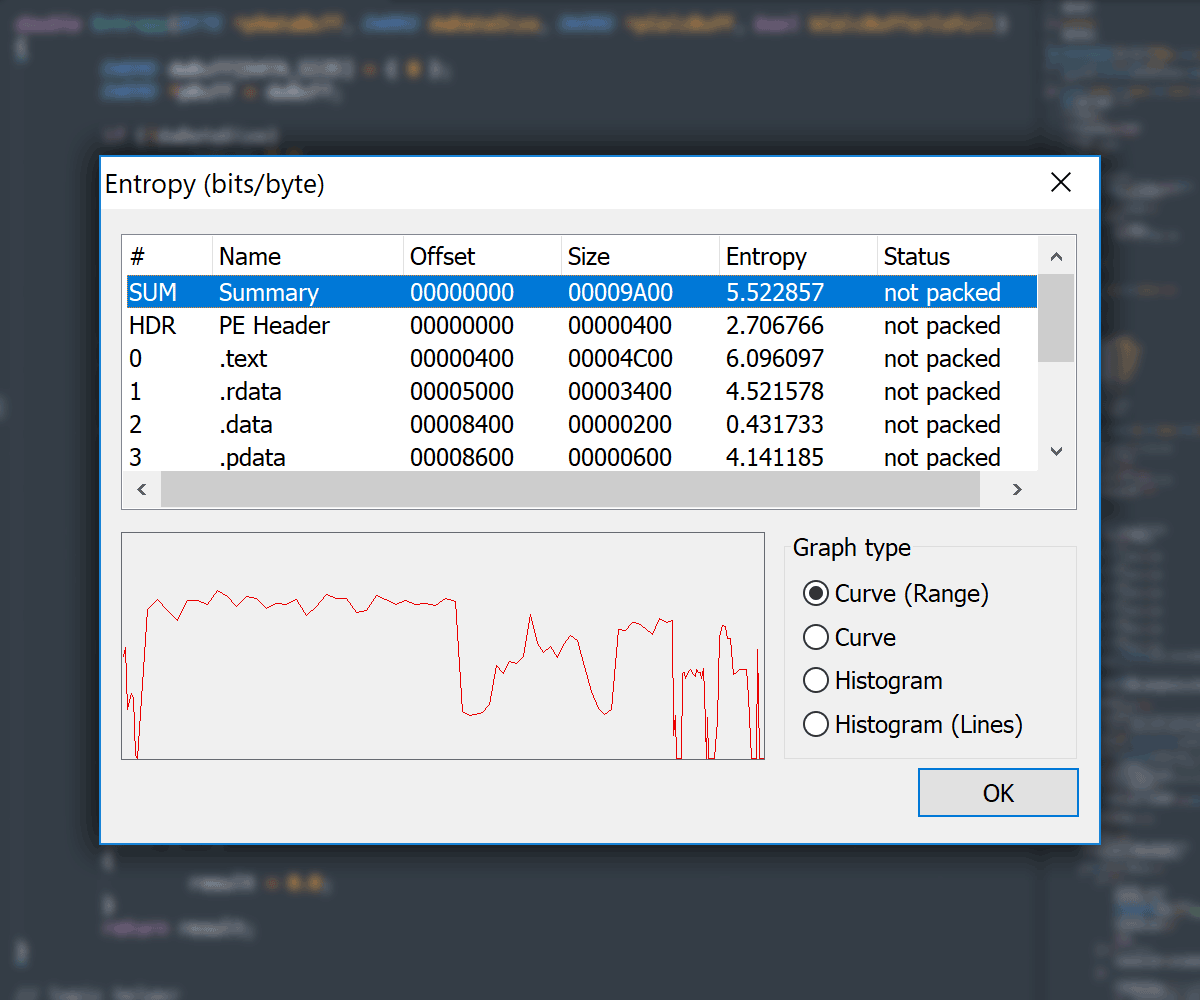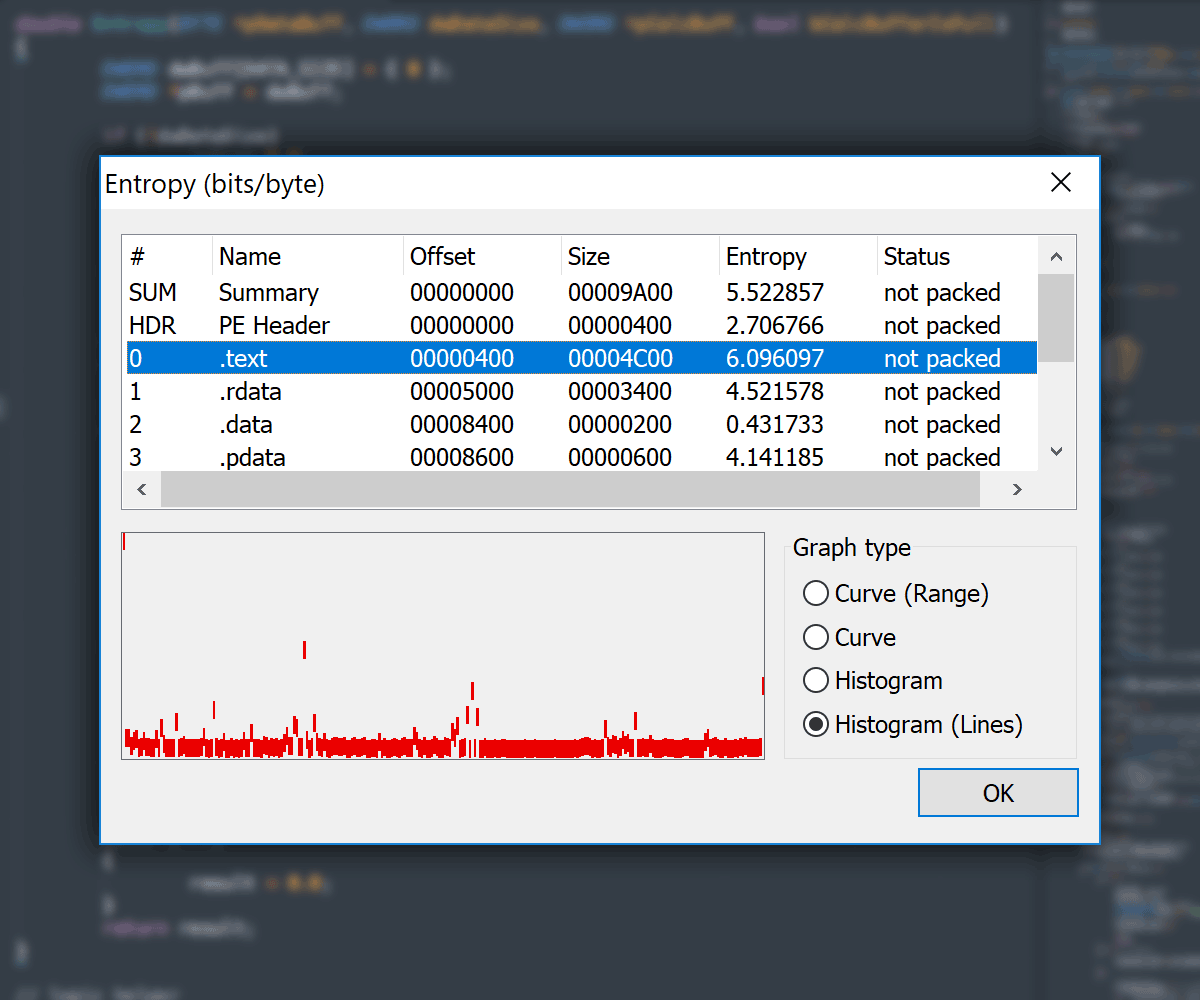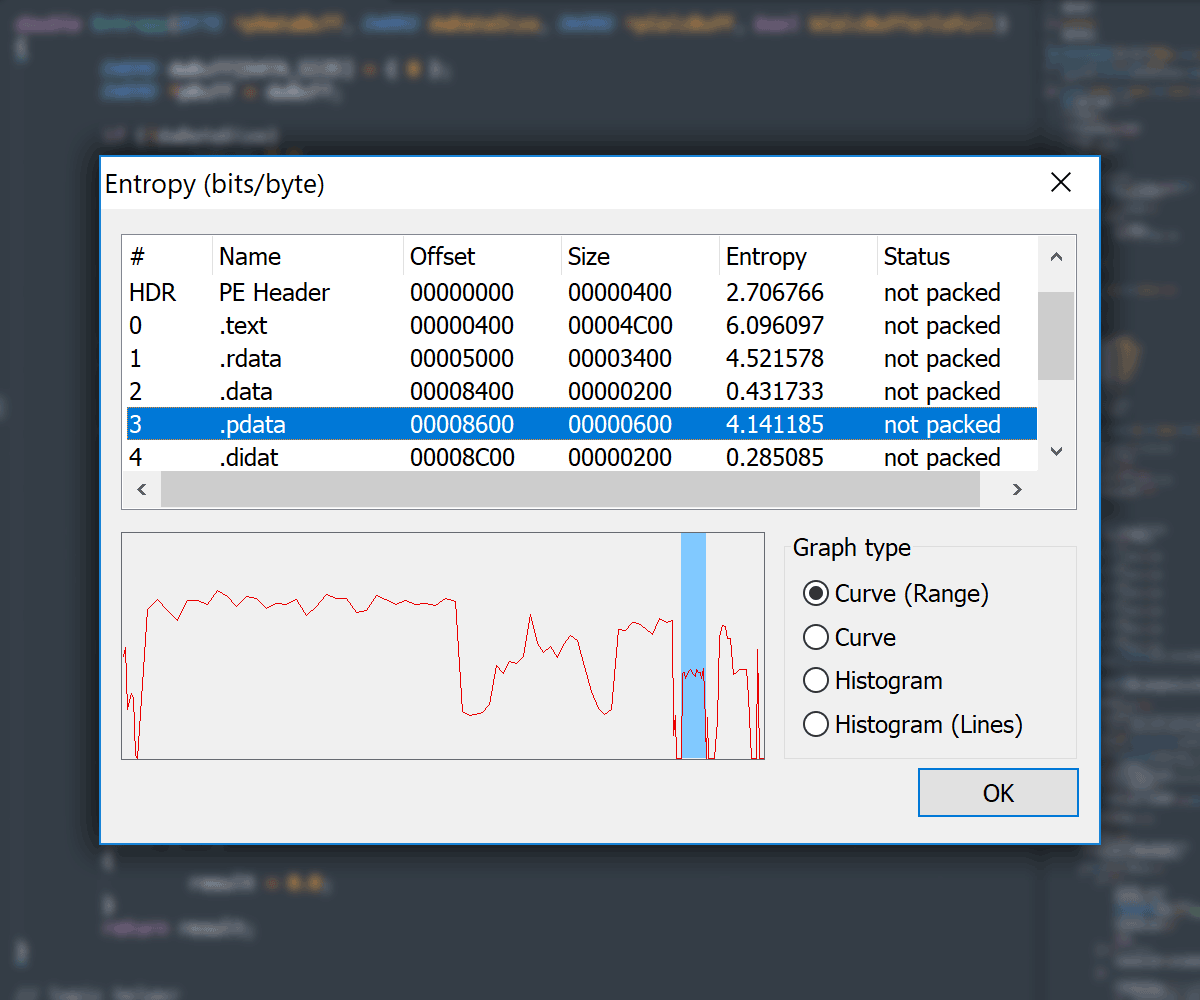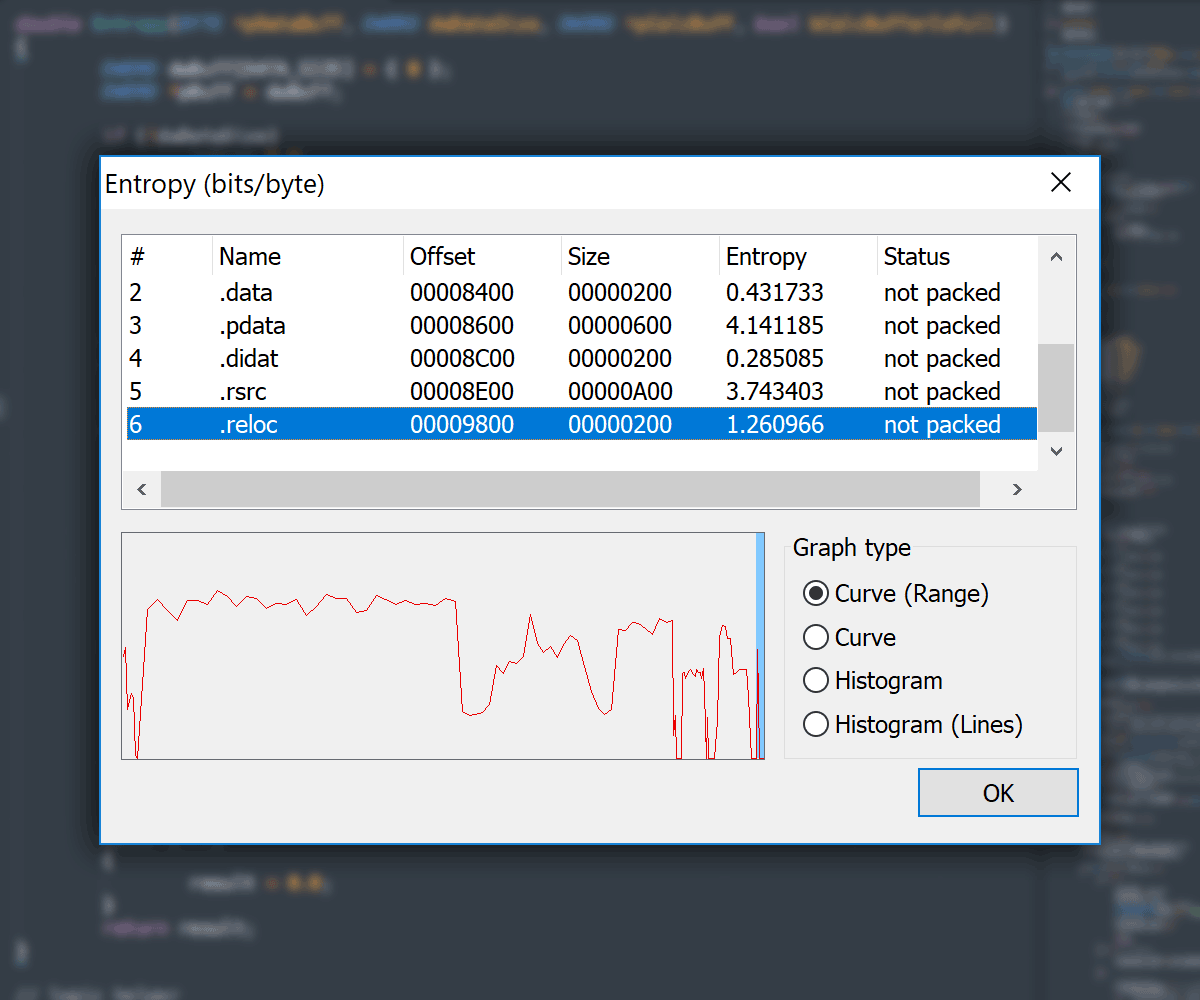
Entropy View
- Entropy Viewer available in:
- Main
PE Editordialog -
Section Editorvia section context menu -
File Comparedialog for both compared files
- Main
64-bit Disassembler
-
diStorm
v3.3.4 - Shows
jmp / calldirection
Load Config Directory Editor
-
IMAGE_LOAD_CONFIG_DIRECTORYsupport - Additional Load Config Directory values and size support (non-standard sizes)
High-DPI display modes support
- 192 DPI supported
-
DPImodes supported and tested:96,120,144,192 - Graphics redrawn:
- Main Application Icon
- Logo
- Toolbar icons
Bug-fixes and minor changes
See HISTORY
System Requirements
- Latest tested Operating System: Windows 10
- Supported Windows versions: Windows 10, Windows 8.1, Windows 8, Windows 7
- Minimal Operating System: Windows XP
- Administrative rights for
SeDebugPrivilege - macOS supported via Wine (tested Wine 3.4, 3.0, 2.16)
- ReactOS natively supported (tested ReactOS 0.4.7)
Limitations
- No large files support (over 4 GB)
- No ARM disassembler support (ARM architecture supported by Windows 10 Mobile, Windows RT, Windows Phone, Windows IoT Core, Windows Embedded Compact)
Source code
throw std::exception(“PE Tools source code is not available”);
- If you want to add some features, write ready-to-use snippet (C/C++) and post it in Issues
To do
- [ ]
Win64version - [ ] File
OverlayAnalyzer and Extractor - [ ]
AuthenticodeViewer - [x]
RichSignature Editor - [ ]
RelocationsChecker - [ ] Enhance
DebugDirectory Remover: remove debug section if empty - [ ] Corkami binaries testing and support
- [ ]
.NET DirectoryViewer - [ ]
External Toolssupport (preliminary list):- [ ] x64dbg
- [ ] Scylla Imports Reconstruction
- [ ] Hiew
- [ ] r2
- [ ] Resource Hacker
- [ ]
Structures Exportto readable formats likeJSON/YAML - [ ]
Cryptotools (hash,decryption/decryption) - [ ]
ARMdisassembler (far-far-away)
Distribution
| File | Description | Lang |
|---|---|---|
PETools.exe |
main PE Tools executable | |
HEdit.dll |
Hex-editor | |
RebPE.dll |
PE Rebuilder | |
Signs.txt |
PEiD signatures for PE Sniffer | |
ReadMe_EN.md |
ReadMe | EN |
WhatsNew_EN.md |
What's New | EN |
WhatsNew_RU.md |
What's New | RU |
petools.sha1 |
Checksums SHA-1 |
DOWNLOAD
Licensing
See LICENSE
Creators
PE Tools
- NEOx [uinC] - versions up to
1.5, 2002-2006 -
Jupiter - versions from
1.5, 2007-2018 - PainteR - versions from
1.8, 2017-2018 -
EvilsInterrupt aka NtVisigoth - versions from
1.5, 2012-2014
Additional modules
- yoda (author of LordPE): original HEdit32 component
Contacts
Feel free to contact via Twitter @petoolse.
Note that the project description data, including the texts, logos, images, and/or trademarks,
for each open source project belongs to its rightful owner.
If you wish to add or remove any projects, please contact us at [email protected].