hashicorp / Terraform Foundational Policies Library
Labels
Projects that are alternatives of or similar to Terraform Foundational Policies Library
Terraform Foundational Policies Library
This repository contains a library of policies that can be used within Terraform Cloud to accelerate your adoption of policy as code. To learn more about the Sentinel language and framework, please review the Sentinel documentation.
Table of Contents
- Prerequisites
- Documentation
- Setup & Integration
- Version Control System (VCS)
- Policy Set Configuration
- Policy Set Management
- Policy Guides
- Useful Resources
Prerequisites
Before you start adopting some of the policies within this library, it is recommended that you do the following:
-
Install the Sentinel CLI. The CLI is an excellent tool for familiarizing yourself with the internals of Sentinel and allows you to
applyandtestpolicies outside of the Terraform platform. You can find more information related to the Sentinel CLI in the Enforce Policy with Sentinel learning track. -
Enable the Governance and Policy Plan in Terraform Cloud.
-
Have access to a supported version control system (VCS) provider.
NOTE: The Governance and Policy Plan is a paid plan in Terraform Cloud. You can learn more about changing your payment plan by reviewing the Changing Your Payment Plan sections in the Terraform Cloud documentation.
Documentation
The file and directory structure within this repository has been designed to have a descriptive ROOT directory that contains all policies that are related to a given standard. As an example, all policies for the Center for Internet Security Benchmarks are all located within the cis directory. Policies are then broken down by cloud service provider (i.e. AWS, Azure and GCP) and then categorized by cloud service (i.e. Compute, Databases, Networking etc.)
.
└── ROOT
└── CLOUD
└── CATEGORY
└── POLICY
└── ...
All CATEGORY related directories contain a single README.md that details all information that is required to assess and enforce a policy in Terraform Cloud. This information includes:
- Policy name
- Description of the controls that are evaluated
- The Policy Set configuration that needs to be added to the
sentinel.hclfile.
Note: You can find a full list of all available policies in the Policy Guides section.
Setup & Integration
Before you can use any of the policies within this library, you will need to configure Terraform Cloud. The following sections detail the high-level steps required to deploy a policy from the foundational policies library. The Enforce Policy with Sentinel learning track covers the end-to-end process in greater detail. If this is the first time you are setting up a Sentinel policy, we encourage you to familiarize yourself with this track prior to continuing further.
Version Control System (VCS)
Terraform Cloud provides first-class support for VCS integration. This allows VCS repositories to contain all of the policies and configuration needed to manage Sentinel policy at scale. Integrating with VCS is as simple as:
- Connect a VCS Provider to Terraform Cloud
- Create a repository in your VCS provider that will be used as the source of your Policy Set configuration
- Clone the source repository to a local directory
Policy Set Configuration
Once the VCS is integrated with Terraform Cloud, start to configure your Terraform Policy Set as follows:
- Identifying a policy from the foundational policies library that should be enforced on a Terraform Workspace
- Review the policy documentation and copy the configuration snippet for the policy of choice.
- Create a
sentinel.hclconfiguration file within the local directory for your repository. - Edit the contents of the
sentinel.hclby pasting the configuration snippet into the body of the configuration file. - Commit your changes to your local repository content and then use the
git pushcommand to upload the changes to your remote repository.
Example Snippet
policy "gcp-cis-7.1-kubernetes-ensure-stackdriver-logging-is-set-to-enabled-on-kubernetes-engine-clusters" { source = "https://raw.githubusercontent.com/hashicorp/terraform-foundational-policies-library/master/cis/gcp/kubernetes/>gcp-cis-7.1-kubernetes-ensure-stackdriver-logging-is-set-to-enabled-on-kubernetes-engine-clusters/gcp-cis-7.>1-kubernetes-ensure-stackdriver-logging-is-set-to-enabled-on-kubernetes-engine-clusters.sentinel" enforcement_level = "advisory" } policy "gcp-cis-7.2-kubernetes-ensure-stackdriver-monitoring-is-set-to-enabled-on-kubernetes-engine-clusters" { source = "https://raw.githubusercontent.com/hashicorp/terraform-foundational-policies-library/master/cis/gcp/kubernetes/>gcp-cis-7.2-kubernetes-ensure-stackdriver-monitoring-is-set-to-enabled-on-kubernetes-engine-clusters/gcp-cis-7.>2-kubernetes-ensure-stackdriver-monitoring-is-set-to-enabled-on-kubernetes-engine-clusters.sentinel" enforcement_level = "advisory" } policy "gcp-cis-7.3-kubernetes-ensure-legacy-authorization-is-set-to-disabled-on-kubernetes-engine-clusters" { source = "https://raw.githubusercontent.com/hashicorp/terraform-foundational-policies-library/master/cis/gcp/kubernetes/>gcp-cis-7.3-kubernetes-ensure-legacy-authorization-is-set-to-disabled-on-kubernetes-engine-clusters/gcp-cis-7.>3-kubernetes-ensure-legacy-authorization-is-set-to-disabled-on-kubernetes-engine-clusters.sentinel" enforcement_level = "advisory" } ...
Policy Set Management
Now that the Policy Set is configured, it is time to enforce this configuration on a Terraform Cloud workspace. This is achieved by:
- Browsing to your Terraform Cloud organization settings
- Browse to Policy Sets settings
- Connect a new Policy Set
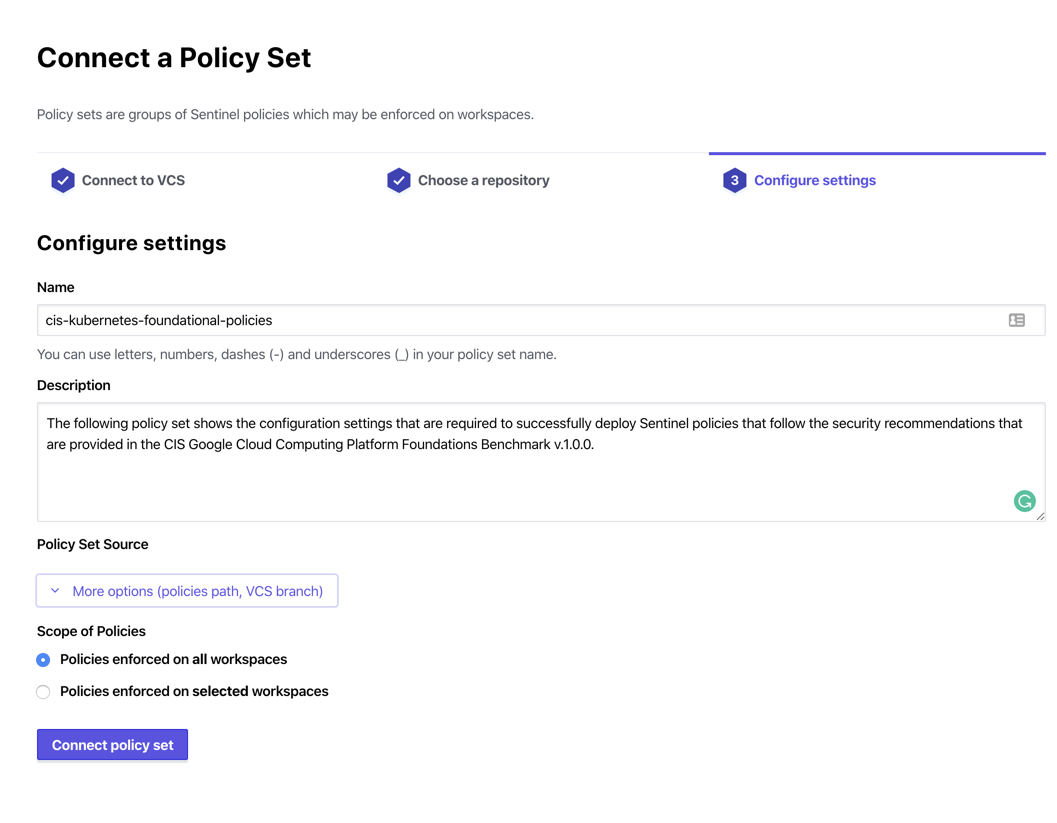
- Configure the Policy Settings (i.e. name, source, path, branch & workspace scope) and apply the settings
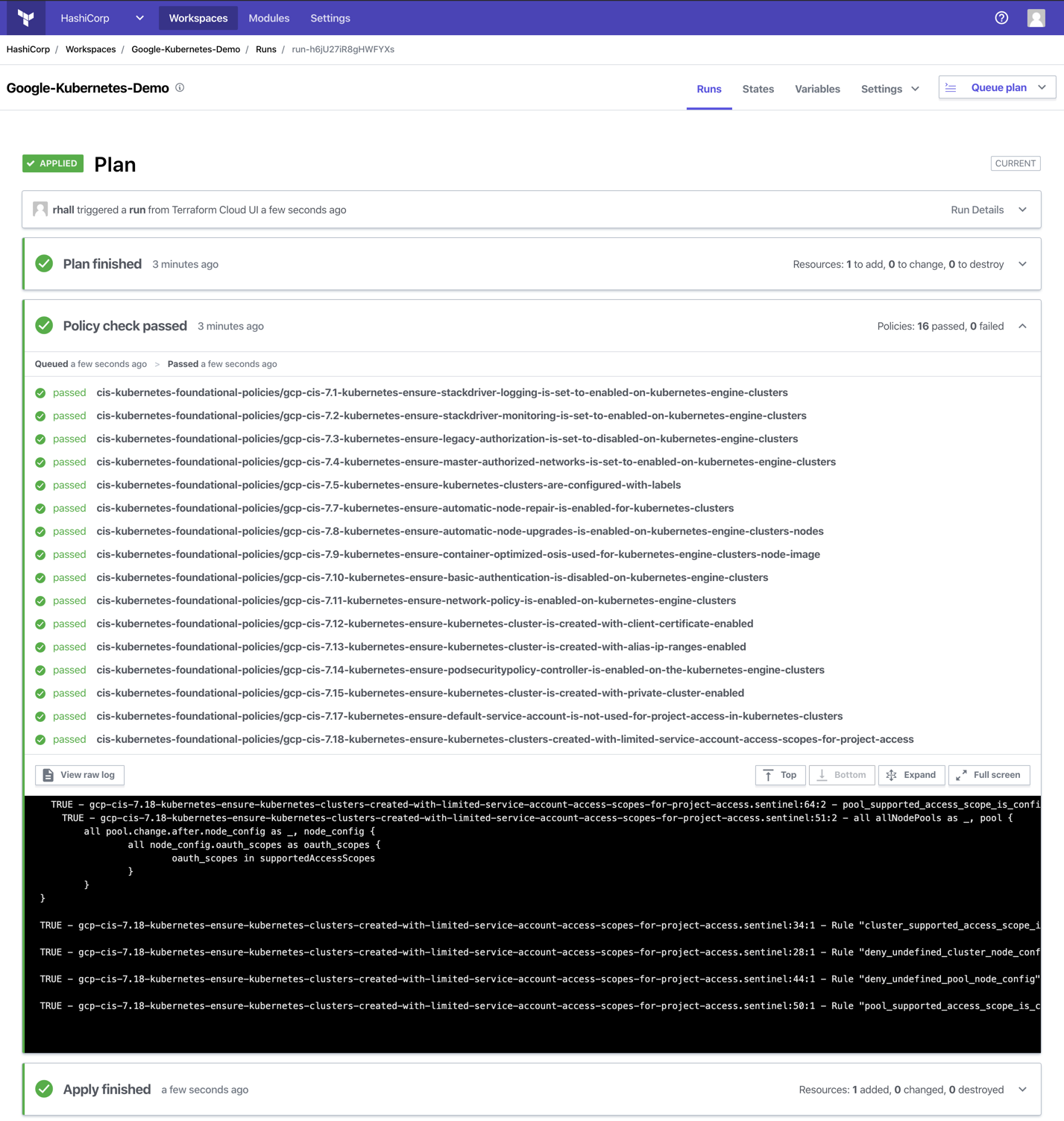
To test the configuration, navigate to the target workspace and queue a new plan. The policy check phase should now appear in the run details, and see the newly created policy will execute and return the state of the policy evaluation (i.e. Pass or Fail).
The image below shows the output of an example policy evaluation:
Policy Guides
Center for Internet Security (CIS)
- Amazon Web Services
- Microsoft Azure
- Google Cloud Platform
Useful Resources
- Getting Started with Terraform Cloud
- Configuring Version Control Access
- Configuring Sentinel Policies
- Sentinel Overview
- Example Policies
- Sentinel Documentation
- Sentinel Language
- Sentinel Language Specification