thalesgroup-cert / Watcher
Programming Languages
Labels
Projects that are alternatives of or similar to Watcher
Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your organisation.
It should be used on webservers and available on Docker.
Watcher capabilities
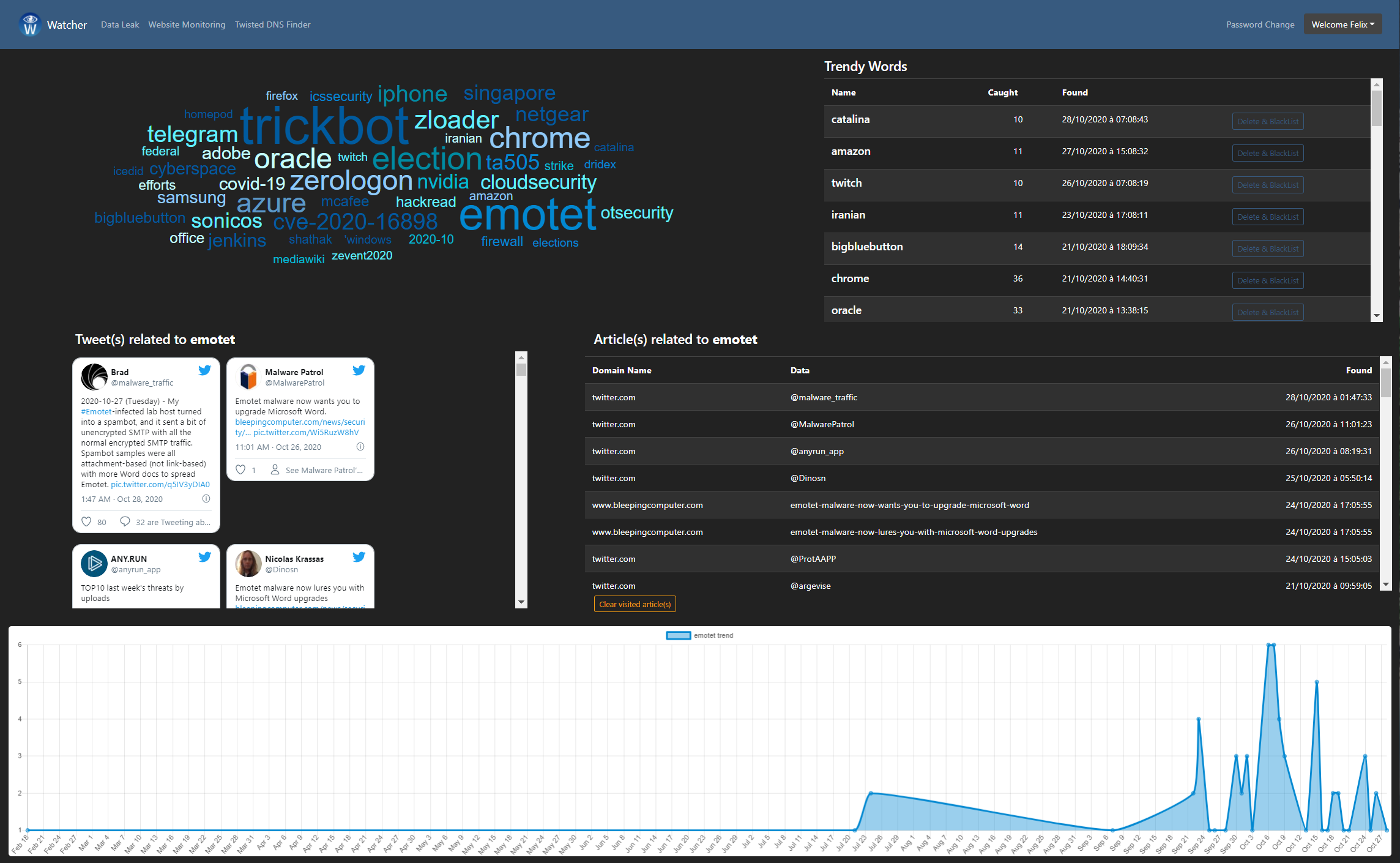
- Detecting emerging cybersecurity trends like new vulnerabilities, malwares... Via social networks & other RSS feeds (www.cert.ssi.gouv.fr, www.cert.europa.eu, www.us-cert.gov, www.cyber.gov.au...).
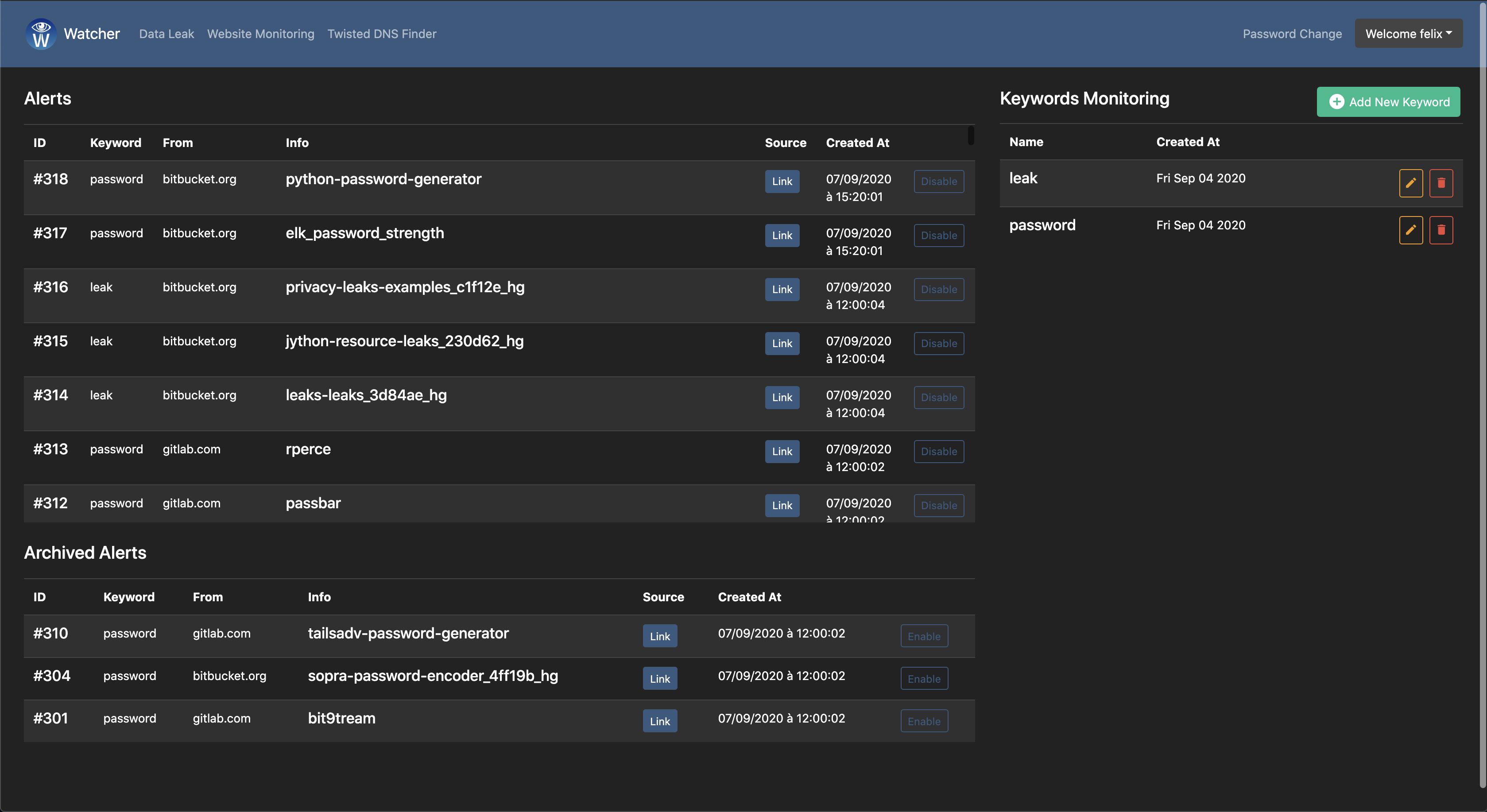
- Monitor for information leaks, for example in Pastebin & other IT content exchange websites (stackoverflow, github, gitlab, bitbucket, apkmirror, npm...).
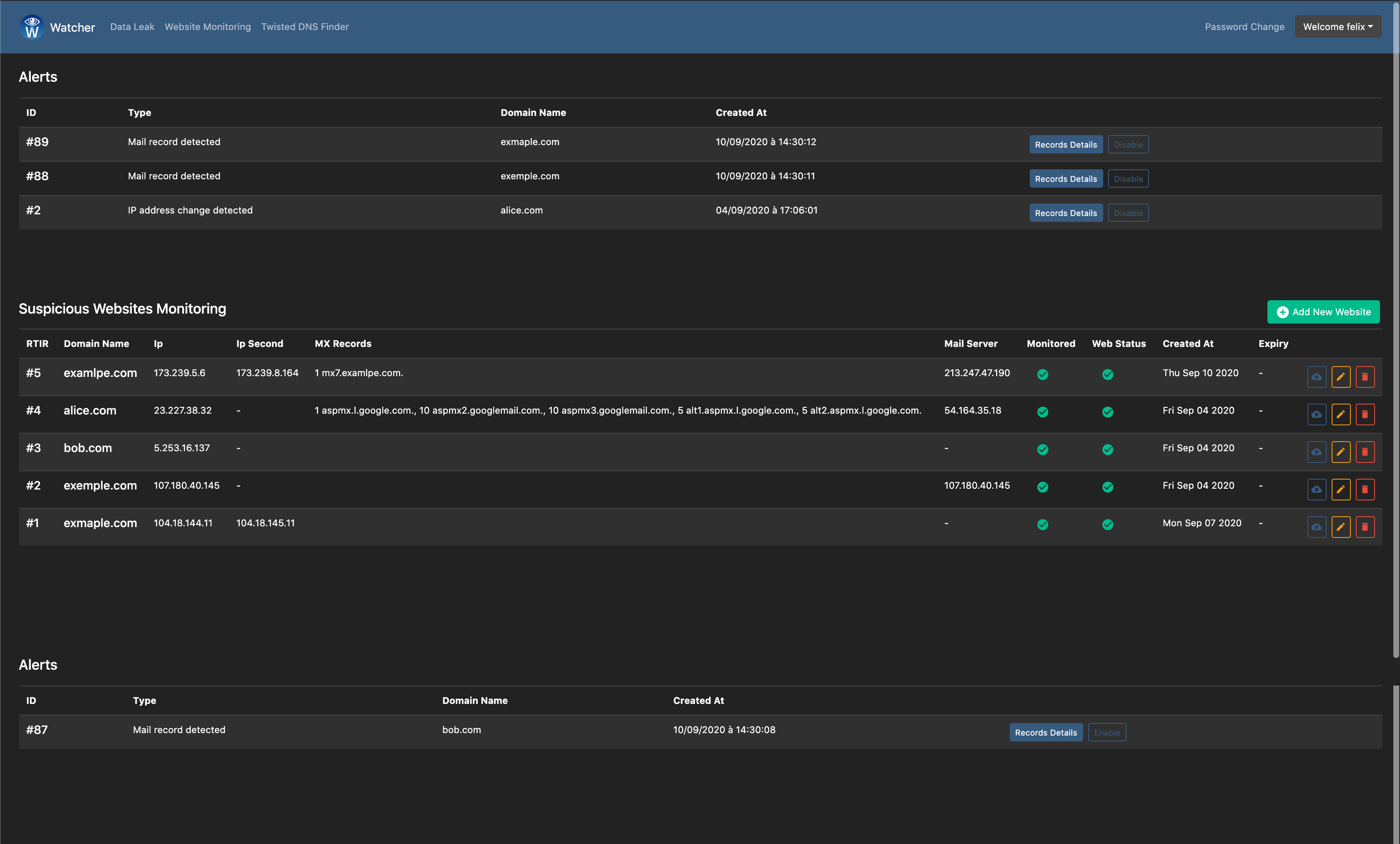
- Monitor malicious domain names for changes (IPs, mail/MX records, web pages using TLSH).
- Detecting suspicious domain names targeting your organisation, using dnstwist.
Useful as a bundle regrouping threat hunting/intelligence automated features.
Additional features
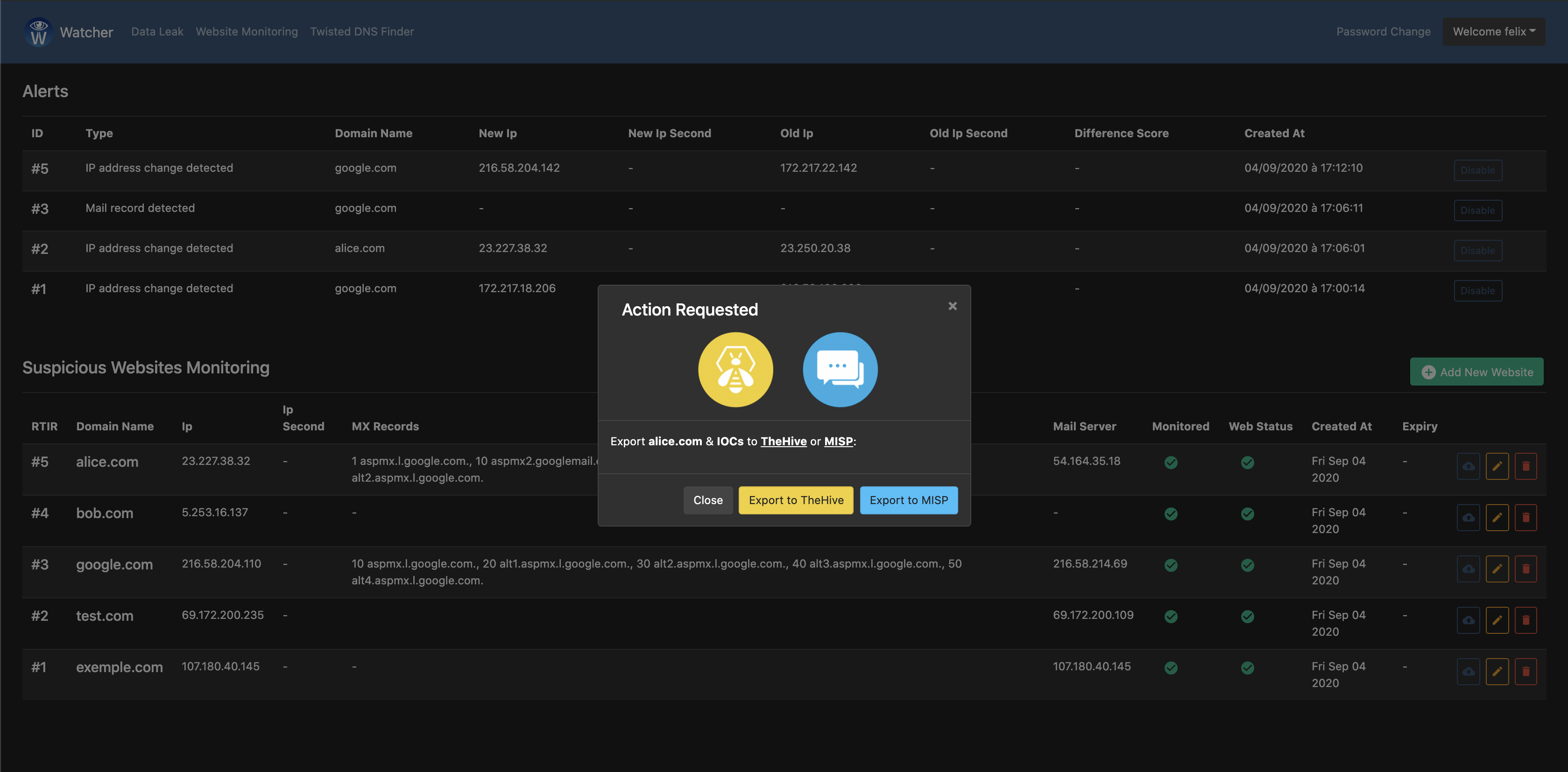
- Create cases on TheHive and events on MISP.
- Integrated IOCs export to TheHive and MISP.
- LDAP & Local Authentication.
- Email notifications.
- Ticketing system feeding.
- Admin interface.
- Advance users permissions & groups.
Involved dependencies
Screenshots
Watcher provides a powerful user interface for data visualization and analysis. This interface can also be used to manage Watcher usage and to monitor its status.
Threats detection
Data leaks
Malicious domain names monitoring
IOCs export to TheHive & MISP
Suspicious domain names detection
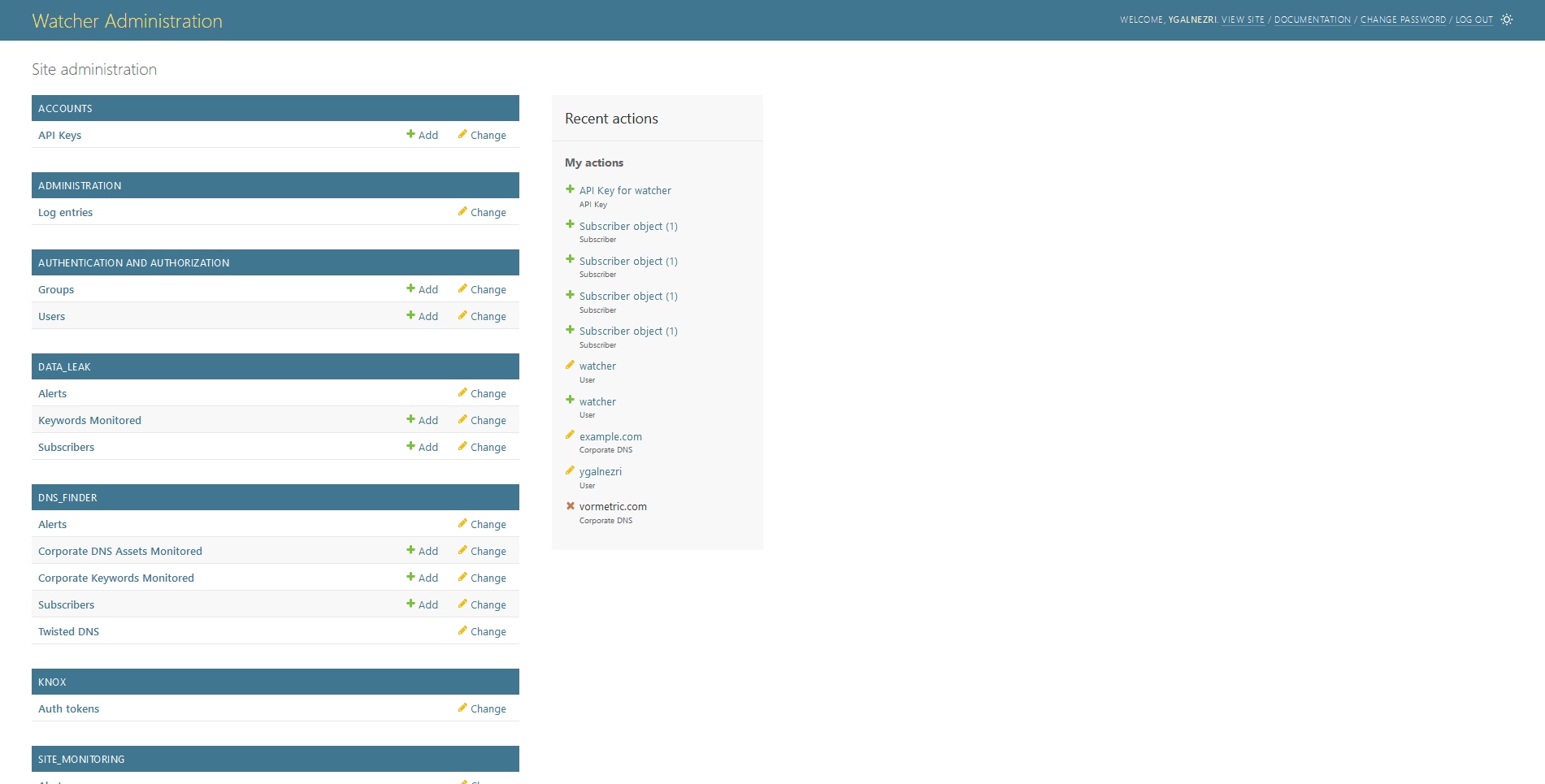
Django provides a ready-to-use user interface for administrative activities. We all know how an admin interface is important for a web project: Users management, user group management, Watcher configuration, usage logs...
Admin interface
Installation
Create a new Watcher instance in ten minutes using Docker (see Installation Guide).
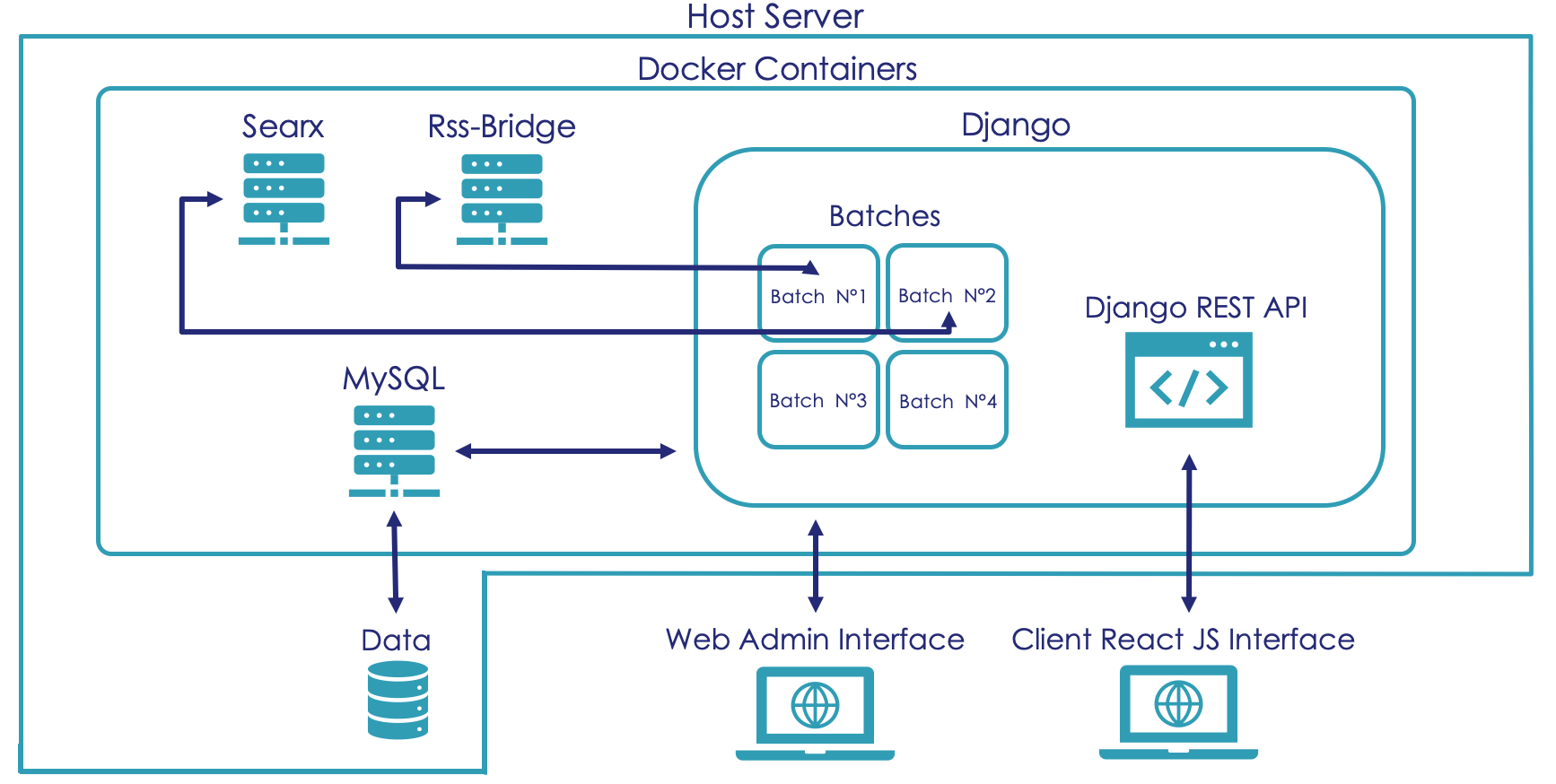
Platform architecture
Get involved
There are many ways to getting involved with Watcher:
- Report bugs by opening Issues on GitHub.
- Request new features or suggest ideas (via Issues).
- Make pull-requests.
- Discuss bugs, features, ideas or issues.
- Share Watcher to your community (Twitter, Facebook...).
Pastebin compliant
In order to use Watcher pastebin API feature, you need to subscribe to a pastebin pro account and whitelist Watcher public IP (see https://pastebin.com/doc_scraping_api).