corneliusweig / Rakkess
Programming Languages
Projects that are alternatives of or similar to Rakkess
rakkess
Review Access - kubectl plugin to show an access matrix for server resources
Intro
Have you ever wondered what access rights you have on a provided kubernetes cluster?
For single resources you can use kubectl auth can-i list deployments, but maybe you are looking for a complete overview?
This is what rakkess is for.
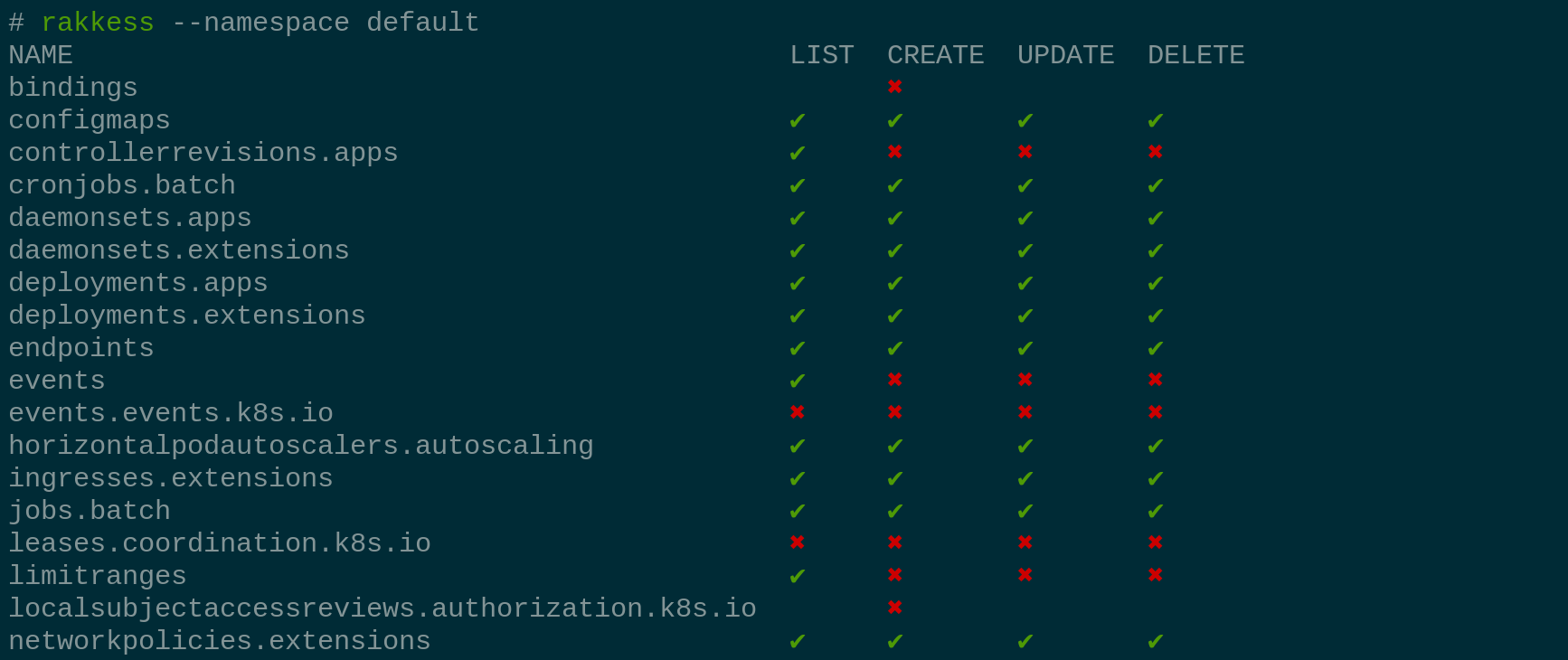
It lists access rights for the current user and all server resources, similar to kubectl auth can-i --list.
It is also useful to find out who may interact with some server resource.
Check out the sub-command rakkess resource below.
Demo
Examples
Show access for all resources
-
... at cluster scope
rakkess
-
... in some namespace
rakkess --namespace default -
... with verbs
rakkess --verbs get,delete,watch,patch -
... for another user
rakkess --as other-user -
... for another service-account
rakkess --sa kube-system:namespace-controller -
... and combine with common
kubectlparametersKUBECONFIG=otherconfig rakkess --context other-context
Show subjects with access to a given resource1
-
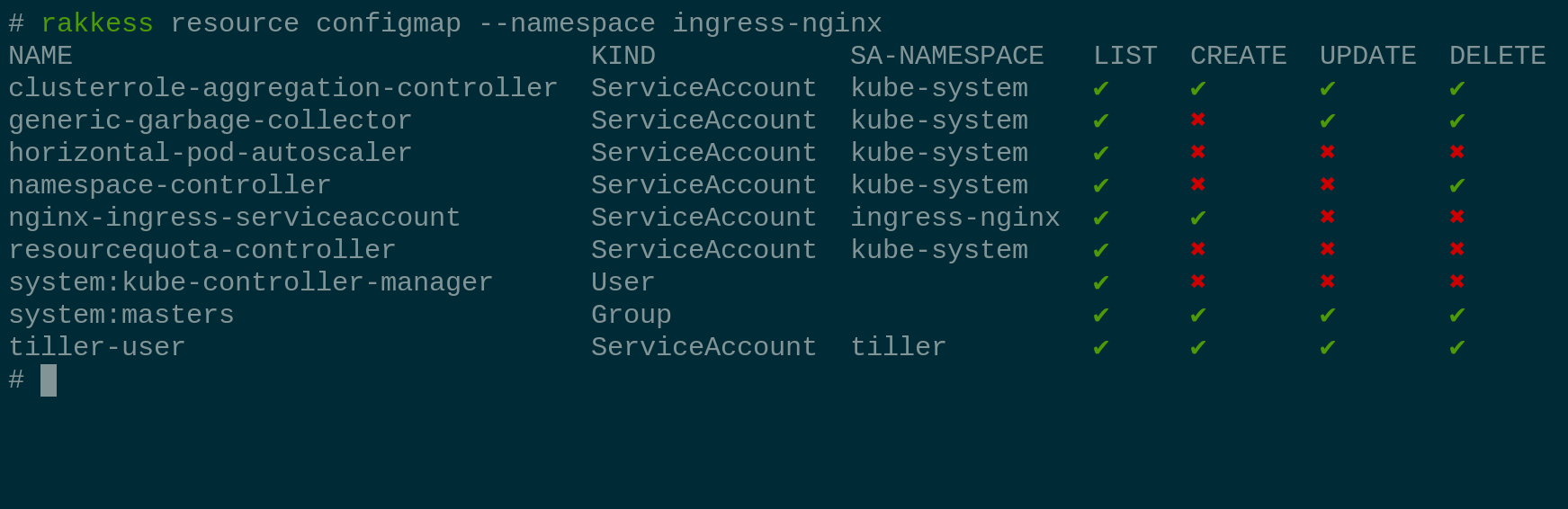
...globally in all namespaces (only considers
ClusterRoleBindings)rakkess resource configmaps
-
...in a given namespace (considers
RoleBindingsandClusterRoleBindings)rakkess resource configmaps -n default -
...with shorthand notation
rakkess r cm # same as rakkess resource configmaps -
.. with custom verbs
rakkess r cm --verbs get,delete,watch,patch
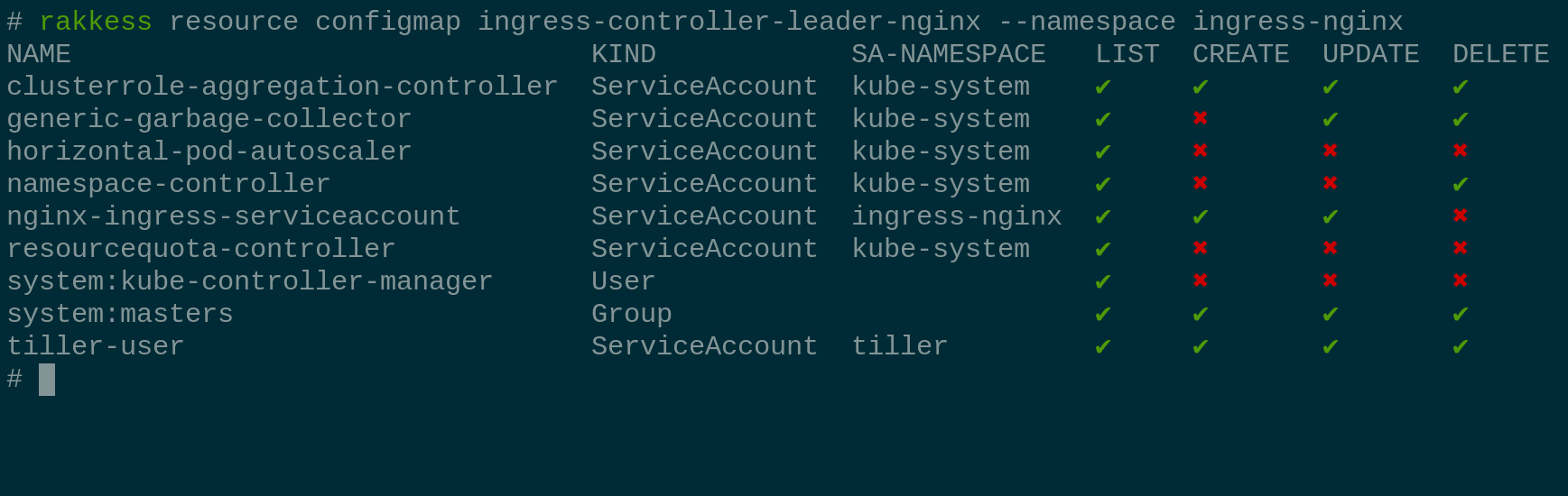
Name-restricted roles
Some roles only apply to resources with a specific name.
To review such configurations, provide the resource name as additional argument.
For example, show access rights for the ConfigMap called ingress-controller-leader-nginx in namespace ingress-nginx (note the subtle difference for nginx-ingress-serviceaccount to the previous example):
As rakkess resource needs to query Roles, ClusterRoles, and their bindings, it usually requires administrative cluster access.
Also see Usage.
Installation
There are several ways to install rakkess. The recommended installation method is via krew.
Via krew
Krew is a kubectl plugin manager. If you have not yet installed krew, get it at
https://github.com/kubernetes-sigs/krew.
Then installation is as simple as
kubectl krew install access-matrix
The plugin will be available as kubectl access-matrix, see doc/USAGE for further details.
Binaries
When using the binaries for installation, also have a look at doc/USAGE.
Linux
curl -LO https://github.com/corneliusweig/rakkess/releases/download/v0.4.7/rakkess-amd64-linux.tar.gz \
&& tar xf rakkess-amd64-linux.tar.gz rakkess-amd64-linux \
&& chmod +x rakkess-amd64-linux \
&& mv -i rakkess-amd64-linux $GOPATH/bin/rakkess
OSX
curl -LO https://github.com/corneliusweig/rakkess/releases/download/v0.4.7/rakkess-amd64-darwin.tar.gz \
&& tar xf rakkess-amd64-darwin.tar.gz rakkess-amd64-darwin \
&& chmod +x rakkess-amd64-darwin \
&& mv -i rakkess-amd64-darwin $GOPATH/bin/rakkess
Windows
https://github.com/corneliusweig/rakkess/releases/download/v0.4.7/rakkess-windows-amd64.zip
From source
Build on host
Requirements:
- go 1.15 or newer
- GNU make
- git
Compiling:
export PLATFORMS=$(go env GOOS)
make all # binaries will be placed in out/
Build in docker
Requirements:
- docker
Compiling:
mkdir rakkess && chdir rakkess
curl -Lo Dockerfile https://raw.githubusercontent.com/corneliusweig/rakkess/master/Dockerfile
docker build . -t rakkess-builder
docker run --rm -v $PWD:/go/bin/ --env PLATFORMS=$(go env GOOS) rakkess
docker rmi rakkess-builder
Binaries will be placed in the current directory.
Users
| What are others saying about rakkess? |
|---|
“Well, that looks handy! rakkess, a kubectl plugin to show an access matrix for all available resources.” – @mhausenblas
|
“that's indeed pretty helpful. rakkess --as system:serviceaccount:my-ns:my-sa -n my-ns prints the access matrix of a service account in a namespace” – @fakod
|
| “THE BOMB. Love it.” – @ralph_squillace |
| “This made my day. Well, not actually today but I definitively will use it a lot.” – @Soukron |
[1]: This mode was inspired by kubectl-who-can